tfvpn – A self-hosted VPN for OSINT investigations
Protect your privacy and keep expenditures low during OSINT investigations with tfvpn, a VPN automation project allowing an effortless deployment of self-hosted VPNs in the cloud.
Tunneling VPN services are indispensable to compartmentalise any sockpuppet personas. The usual solution for maintaining a good OPSEC hygiene is a tunnelling VPN service of some sort. There are several commercial and self-hosted VPN solutions available allowing to obfuscate the real IP address of the OSINT investigator.
The problem with VPN services
No matter if you side with commercial VPN services or homebrew solutions, they both have potential risks and disadvantages:
- Relatively high cost;
- Privacy and security risks; and
- Constraints around flexibility.
Let’s see what these disadvantages are and how the tfvpn project attempts to solve them!
Cost and security
One of the limiting factors of commercial VPNs is cost. At the time of writing, ExpressVPN charges $12.95 per month for a no-commitment 1-month plan. It may not sound a lot first, but it costs more than Netflix and the expenses can add up over time.
The second disadvantage of commercial VPNs is the privacy risks they pose. Although most VPN providers boast their strict no-logging policy, security breaches or security misconfigurations can expose the OSINT investigator on the internet when things go awry.
In a nutshell, consumers of paid VPN services have little to no visibility and control of the inner workings of the service even though the premium price they pay.
Time-consuming deployment
Self-hosting a VPN service could alleviate the cost issues and privacy risks outlined above.
Open-source VPN projects (such as hwdsl2/setup-ipsec-vpn, Streisand or algo) usually involve running a Linux-based virtual machine (VM) at a cloud provider.
As budget cloud providers typically charge around U$5/mo for a virtual machine, it makes these projects more competitive in terms of cost compared to commercial VPN.
The open-source projects above implement some level of automation for making the installation and configuration of the underlying VPN applications (e.g. WireGuard, StrongSwan, OpenVPN) easier. Unfortunately, the automation does not cover everything as the hosting infrastructure itself (i.e. virtual machine) has to be manually deployed and pre-configured before the automation scripts can be launched.
The lack of full automation impacts flexibility. For instance, if we wish to relaunch the VPN service in a different geographical region, we need to go through the tedious manual process again.
Scripting VPN deployments with tfvpn
What if we could combine the flexibility of:
- Commercial VPNs (multiple regions, easy setup and maintenance, set and forget approach); and
- The privacy and cost benefits of a self-hosted VPN service?
The solution is infrastructure automation.
The tfvpn project (link) relies on Terraform, a popular IaC automation tool allowing fast and repeatable deployment of cloud environments.
tfvpn allows rapid deployment of the hosting cloud infrastructure required self-hosted VPNs. The project relies on the hwdsl2/setup-ipsec-vpn project and it deploys an IPSec VPN on the Linode (referral link) cloud.
tfvpn project benefits
The advantages of a tfvpn VPN over commercial VPNs are the following:
- Cost savings by terminating the self-hosted VPN when not in use; and
- Reduced privacy risks due to self-hosting.
The advantages of a tfvpn VPN over manually deployed self-hosted VPNs:
- Rapid deployment;
- Fast redeployment (e.g. to change the terminating IP address); and
- Easy termination of the hosting infrastructure to save costs when the VPN is not in use.
How to deploy your first tfvpn
These steps allow you to deploy a fully functioning self-hosted IPSec VPN service on Linode. The hosting infrastructure can be destroyed with one click to save costs, or redeployed to change the terminating IP address and/or geographical location where the VPN service is running.
The following instructions assume that the reader is familiar with the basic operation of git and Terraform.
-
Install the Terraform CLI on your PC or Mac;
-
Clone the repository:
git clone https://github.com/gszathmari/tfvpn.git -
Change your working directory:
cd tfvpn/ -
Initialise Terraform before the first use:
terraform init -
Then run
terraform applyto launch the hosting infrastructure:terraform apply -
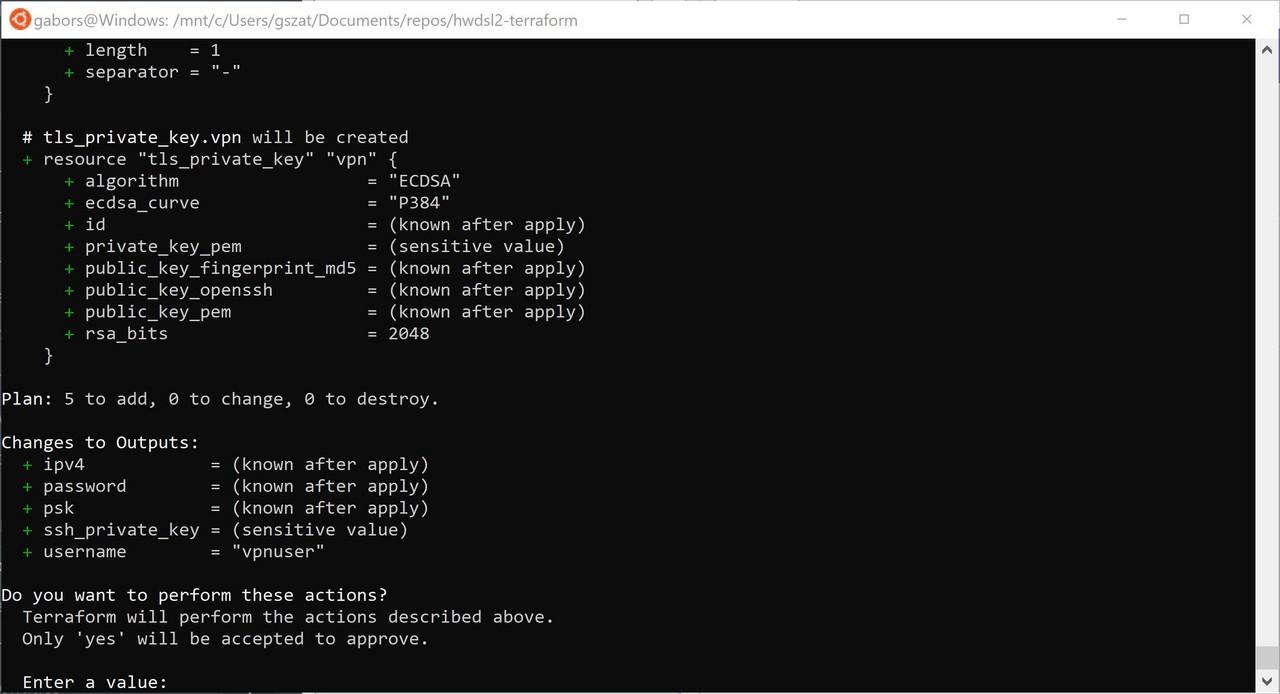
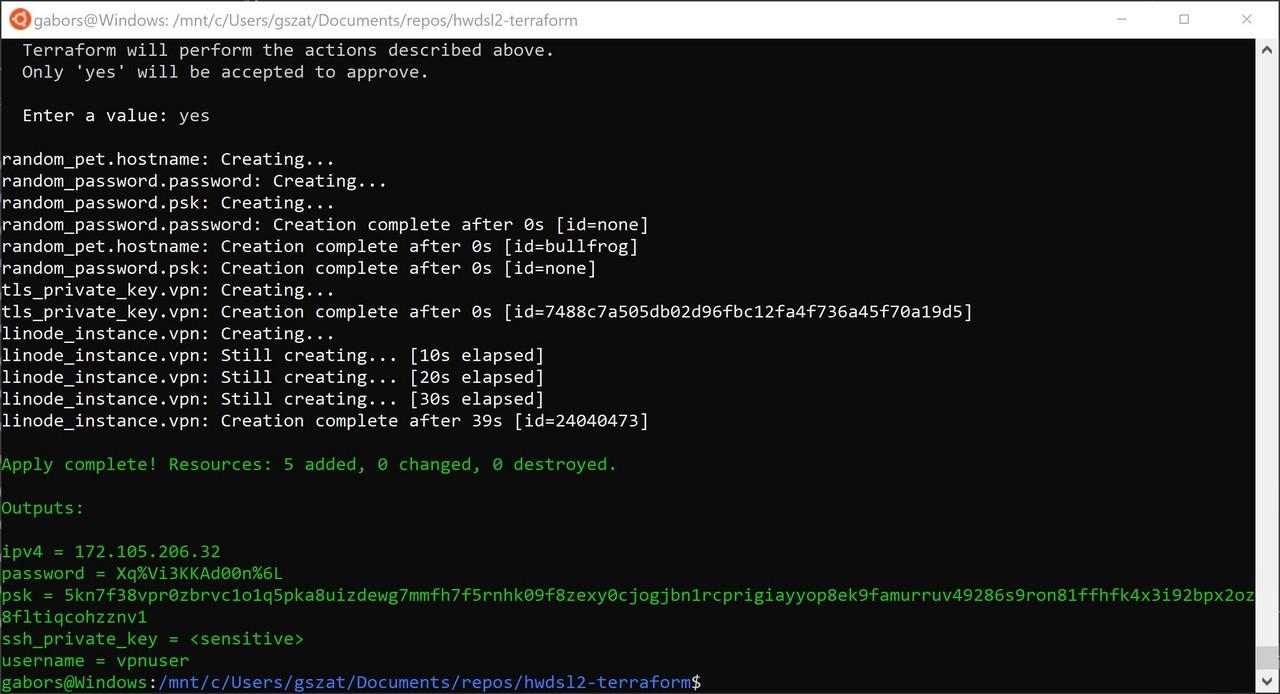
Enter your Linode API key when prompted.
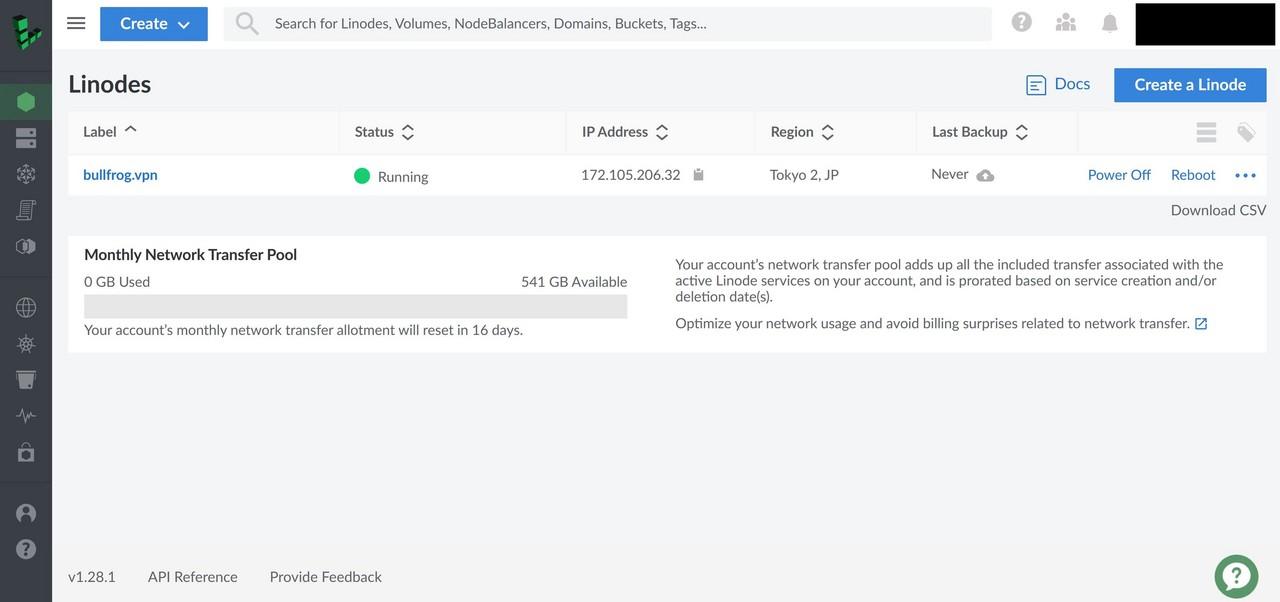
Answer yes to confirm the deployment. If everything ran successfully, the Linode dashboard should display the virtual machine running our new VPN service.
Once Terraform finishes the deployment of tfvpn, wait a minute or two and your VPN service is ready to accept new connections.
The VPN connection details (IP address, username and password) are displayed on the terminal screen.
Client configuration
To configure Windows, Linux, macOS, iOS and Android clients, refer to the hwdsl2 client configuration guide. Use the connection parameters shown on the terminal screen from the previous step.
Destroying the VPN
If your tfvpn VPN service is no longer needed, it is easy to delete everything with Terraform again:
-
Change your working directory:
cd tfvpn/ -
Run Terraform with the
destroyparameter this time.terraform destroy -
Enter the Linode API key and answer ‘yes’ to confirm the deletion of your hosting infrastructure.
Once Terraform manages to clean up the virtual machine, Linode should stop billing for the service.
Redeploying the service
To switch to a new IP address in the same geographical region (tfvpn defaults to Tokyo, JP), simply run terraform apply after a successful destroy step. Linode will assign a fresh, random IP address to the new virtual machine running your VPN service.
Choosing a different region
If you wish to deploy the VPN service into a different Linode region (e.g. “us-east”, “ca-central”, “ap-south”), you need to specify the -var switch:
terraform apply -var='region=ca-central'
For a list of Linode regions, please refer to the output of this API call.
Summary
The tfvpn project further automates the deployment of open-source VPN solutions. It provides more flexibility and reduced IT costs to those relying on VPN tunnels for their OSINT investigations.