BulletProftLink - A phishing service from Malaysia (Part 2)
How the phishing campaigns ran by ‘thegreenmy87’ is linked to a bulletproof hosting provider? Who is responsible for the phishing campaigns facilitating identity theft? How could we pinpoint an individual behind ‘Anthrax Linkers’? We provide further insight into a long-running scam operation in this article.
This is a multipart article. Please click here to read Part 1 of the series.
Links to a bulletproof provider
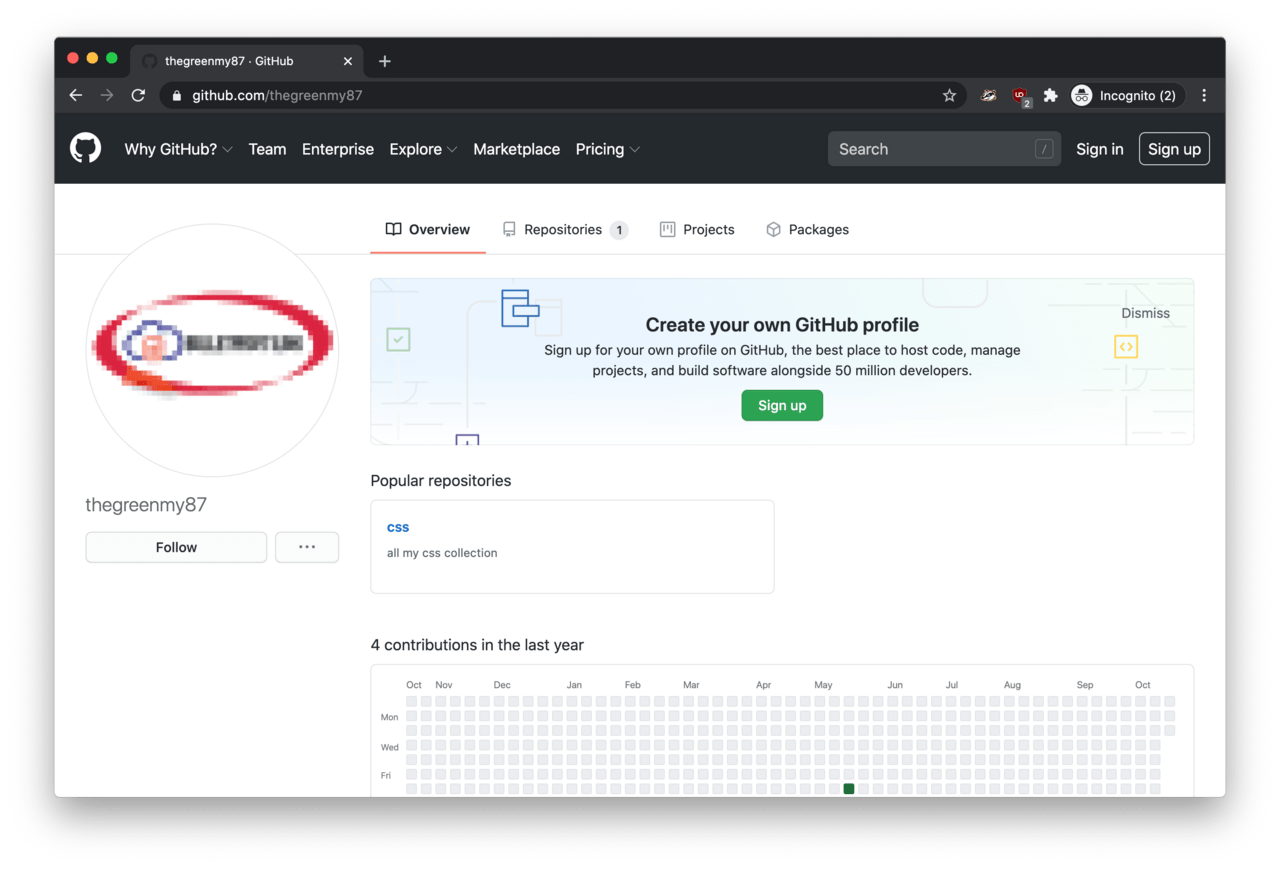
In the previous article, we established that ‘thegreenmy87’ and ‘Anthrax Linkers’ are both somehow associated with phishing activity. We found the GitHub and Gravatar accounts of thegreenmy87 but did not look into the latter yet.
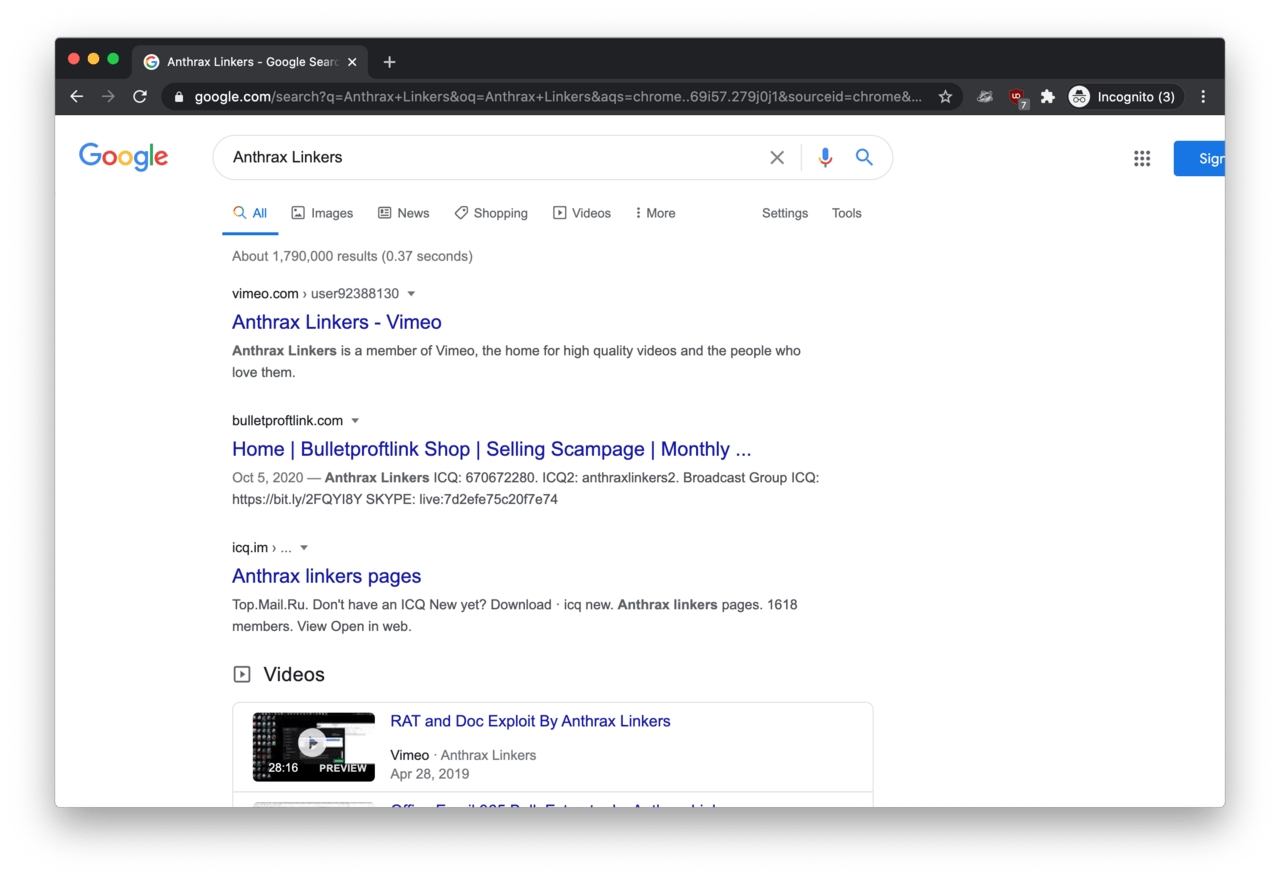
So Googling ‘Anthrax Linkers’ was rather successful. On the first page of results, the second hit was a website called Bulletproftlink Shop hosted on https://bulletproftlink.com/.
The dissection of Bulletproftlink
Remember Bulletproftink.com/shop from the video description on UKBlow? It turns out the URL had a typo in it (doh!).
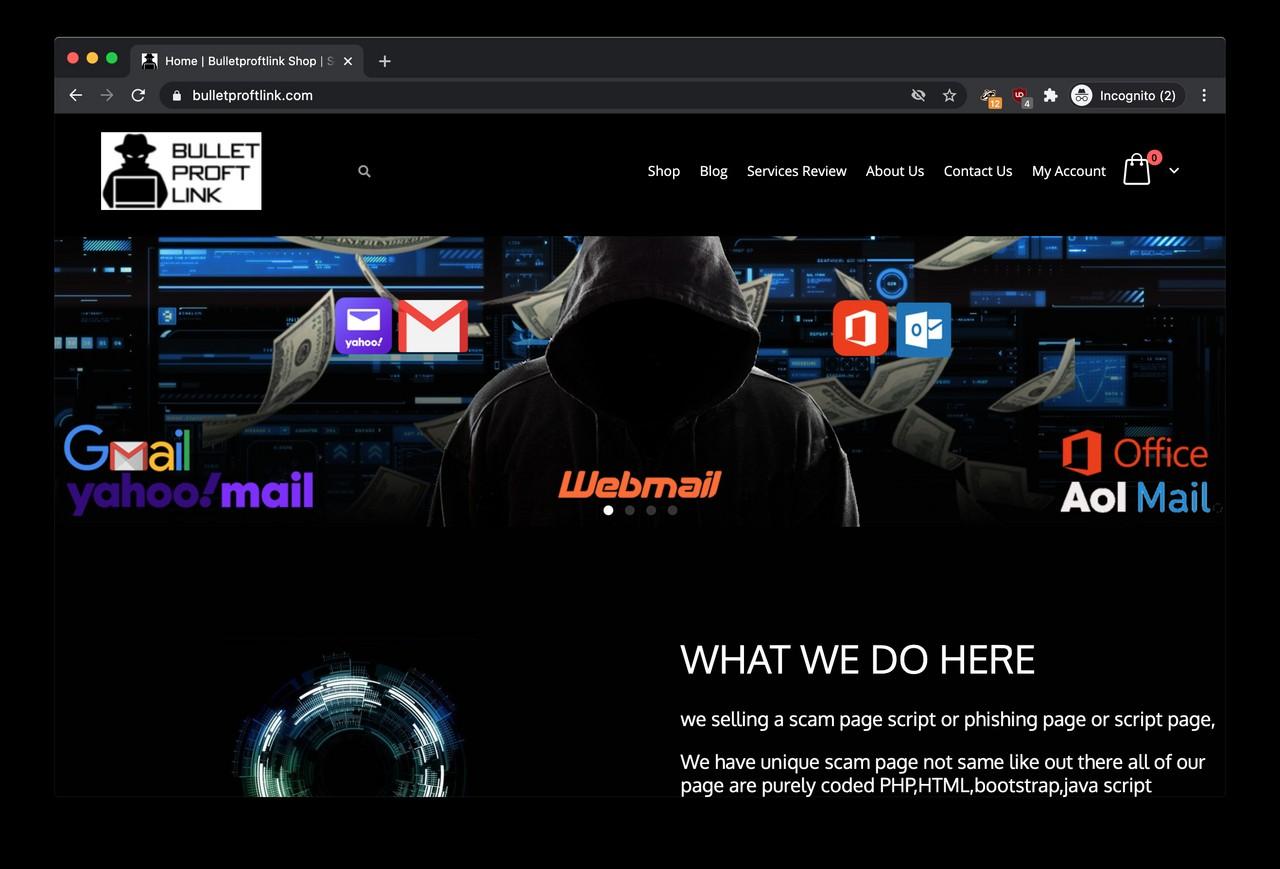
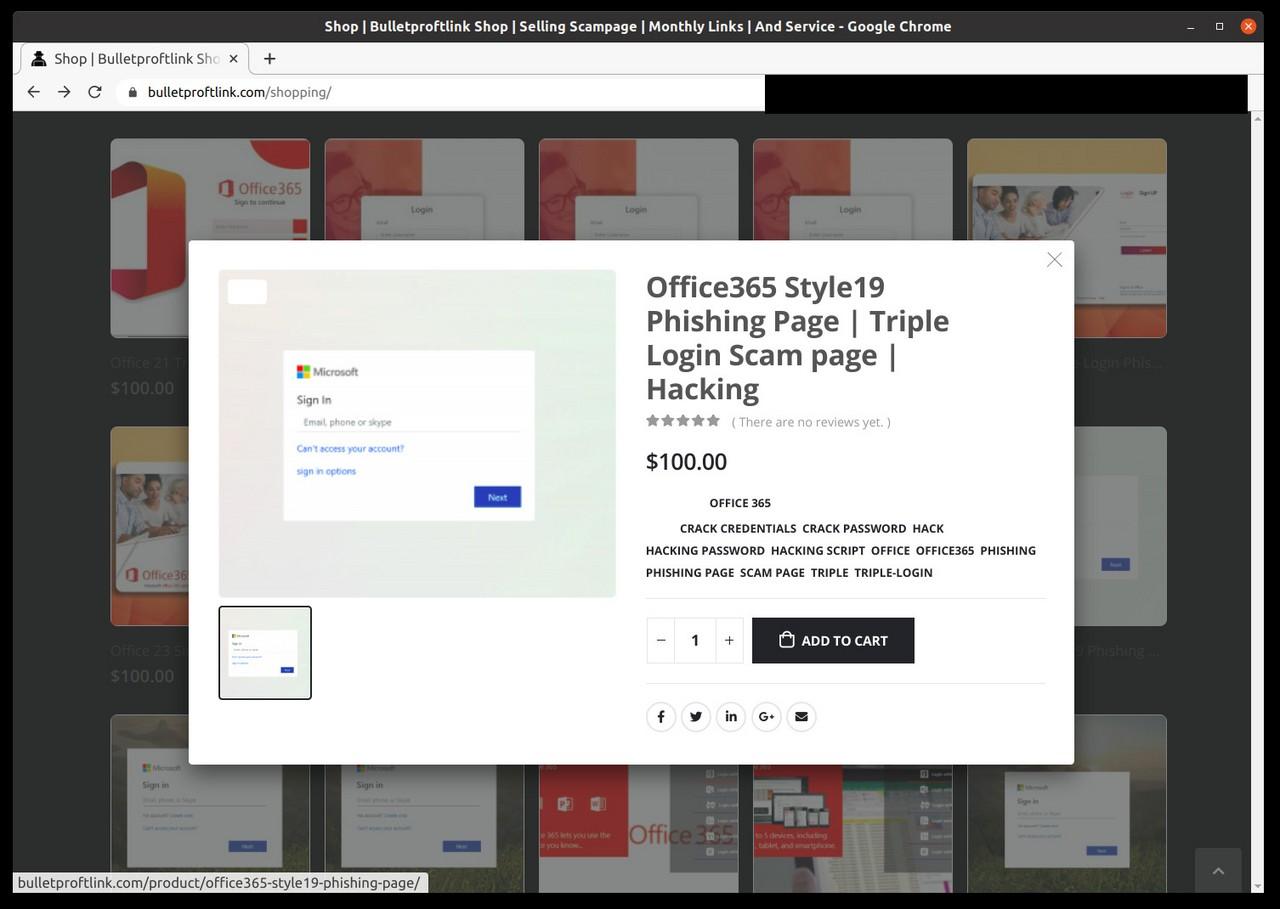
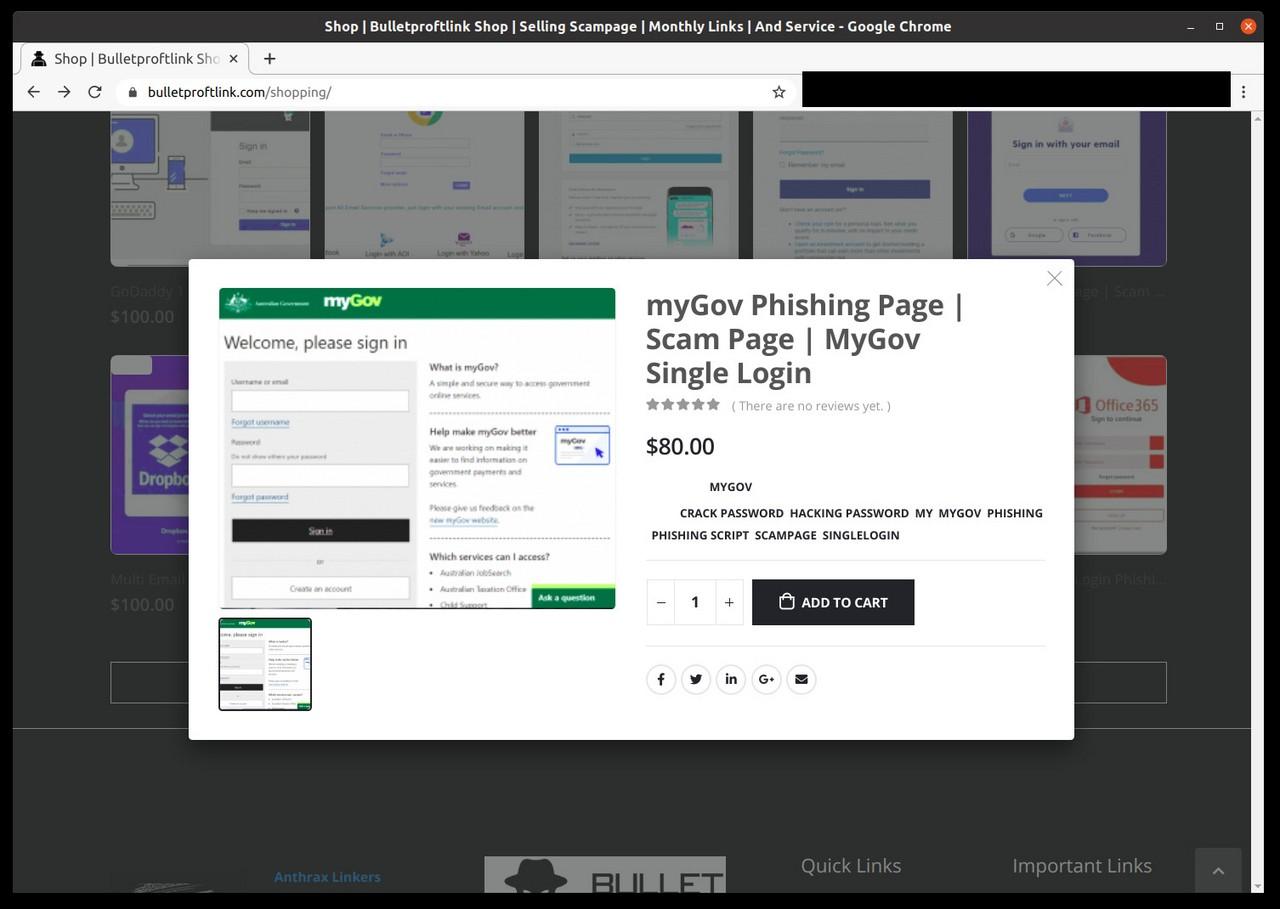
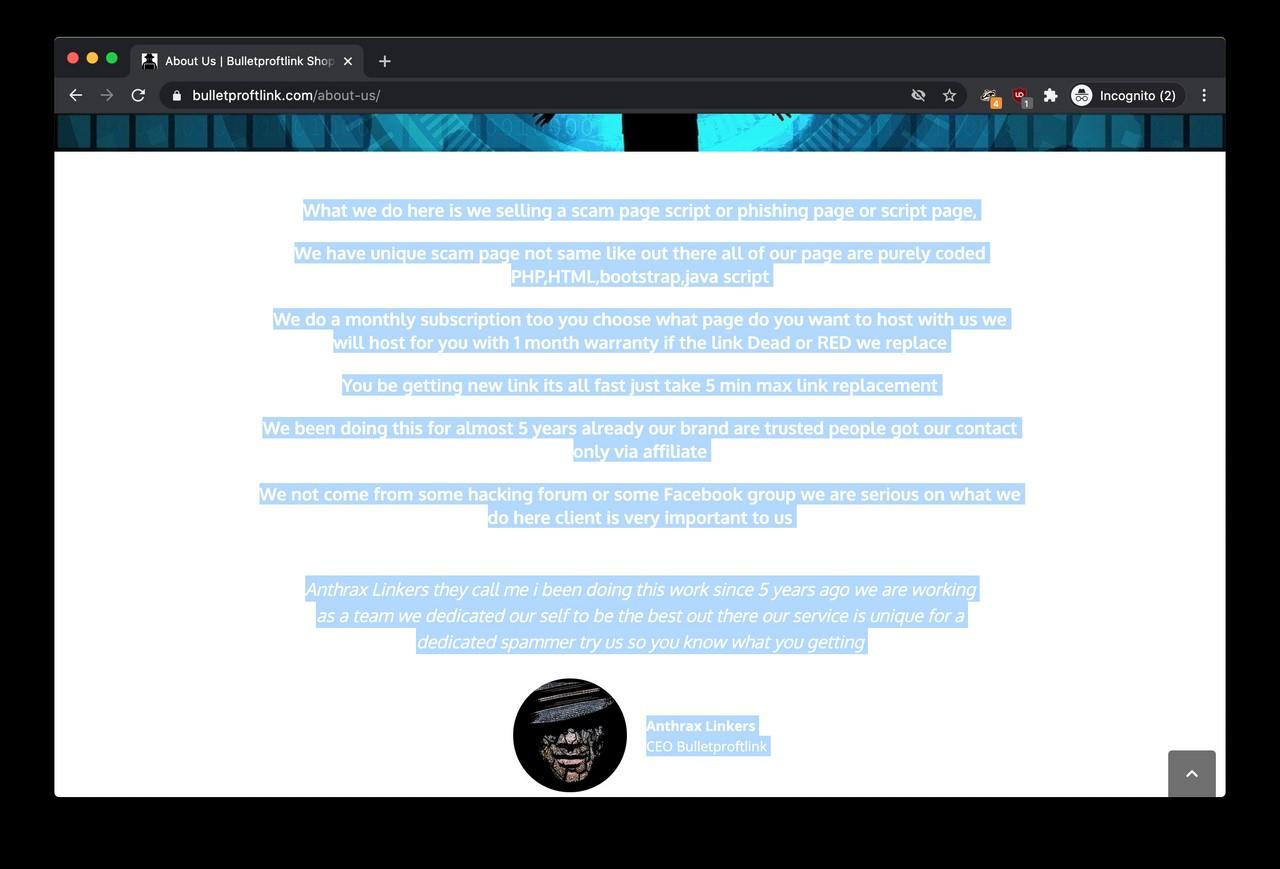
So the actual Bulletproftlink on bulletproftlink.com is essentially a webshop “selling a scam page script or phishing page or script page”. The website is selling complete, downloadable webpages impersonating login pages of well-known brands and services, such as the Chase Bank, Adobe, American Express, Office 365, myGov (Australia), webmail providers like Yahoo, Outlook and many more.
Each product costs around $100 and payment methods include credit card and Bitcoin.
Managed phishing services
The website also offers “a monthly subscription too you choose what page do you want to host with us we will host for you” aka. hosting the phishing pages for a monthly flat fee. According to the ‘About us’ page, “we been doing this for almost 5 years”. This information should be taken with a grain of salt as Bulletproftlink is online since 2018 according to the Internet Archive.
Connections with Anthrax Linkers
According to the footer of the website, Bulletproftlink is run by individual or individuals from Anthrax Linkers. The Telegram, ICQ and Jabber accounts are all referencing the name of the adversary.
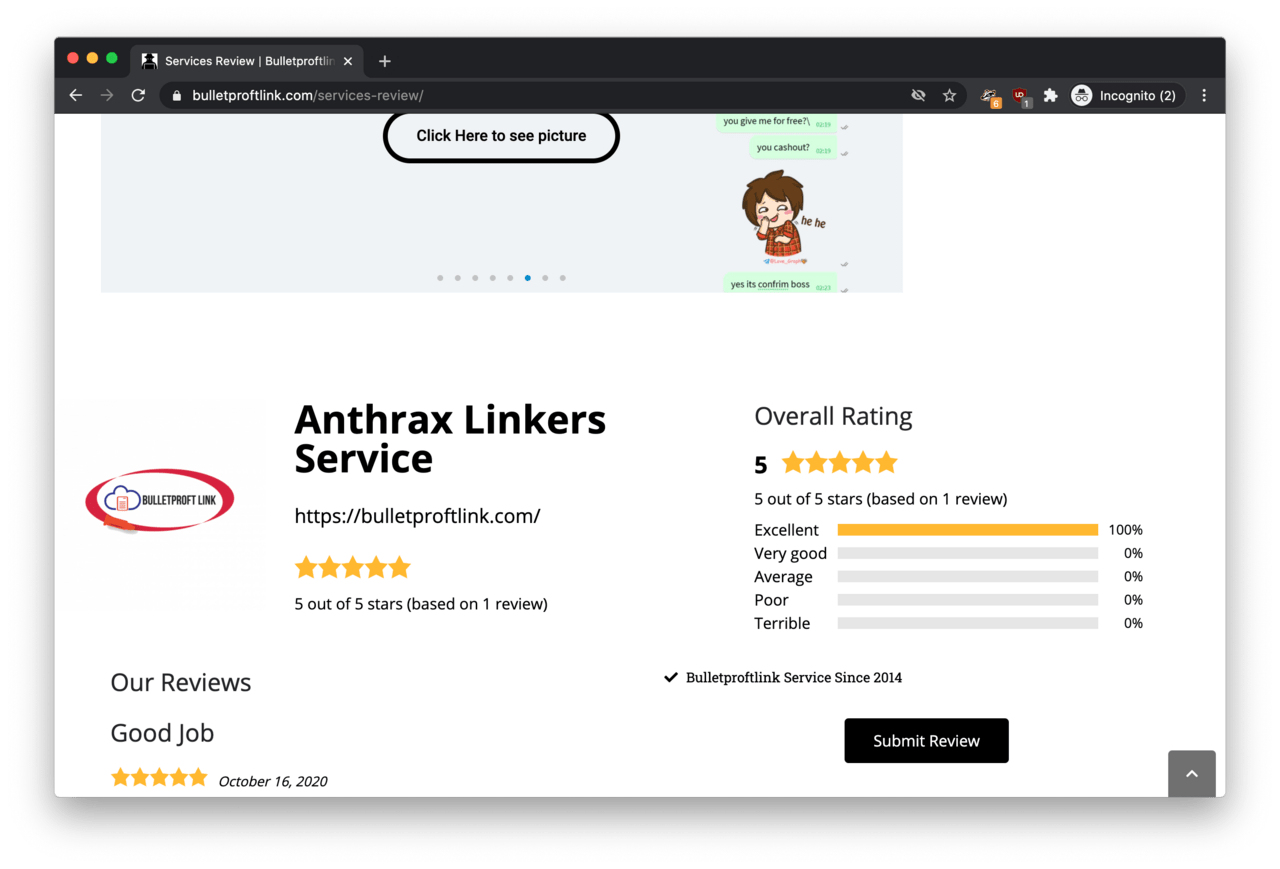
The connection with Anthrax Linkers is further confirmed if we go to https://bulletproftlink.com/services-review/, where Bulletproftlink is described as an ‘Anthrax Linkers Service’ where a familiar logo shows up.
Also, remember the low-res image from Gravatar and GitHub.com associated with thegreenmy87? The ‘Services Review’ page features the same logo in high resolution! It says: ‘Bulletproft Link’.
Managed phishing service for hire
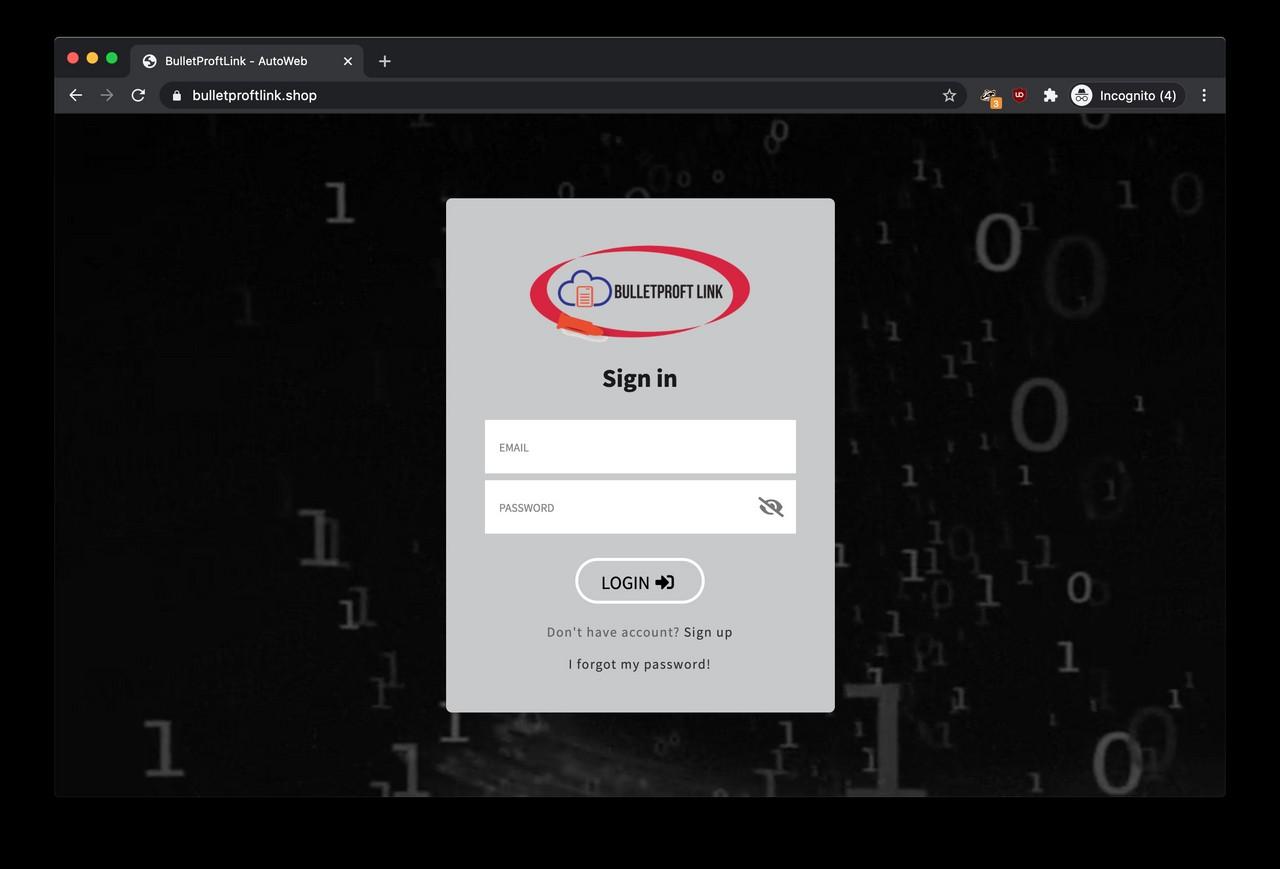
A further Google research led us to a familiar login page running at https://www.bulletproftlink.shop/ featuring the ‘Bulletproft Link’ logo. This login page is the gateway to the subscription-based bulletproof hosting service referenced by the main website.
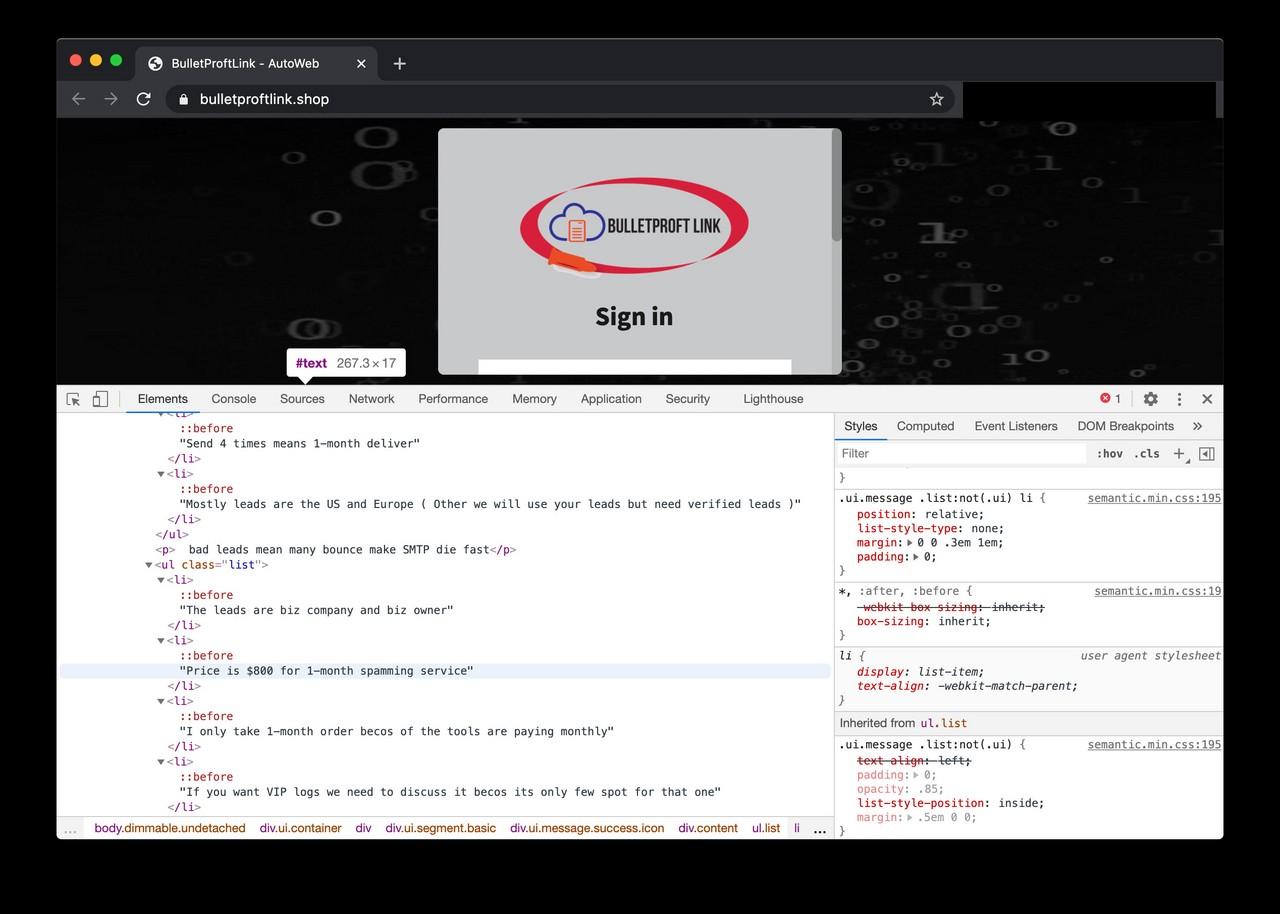
Interestingly, if we fire the web inspector, the page DOM gives us a candid insight into the services offered behind the login page.
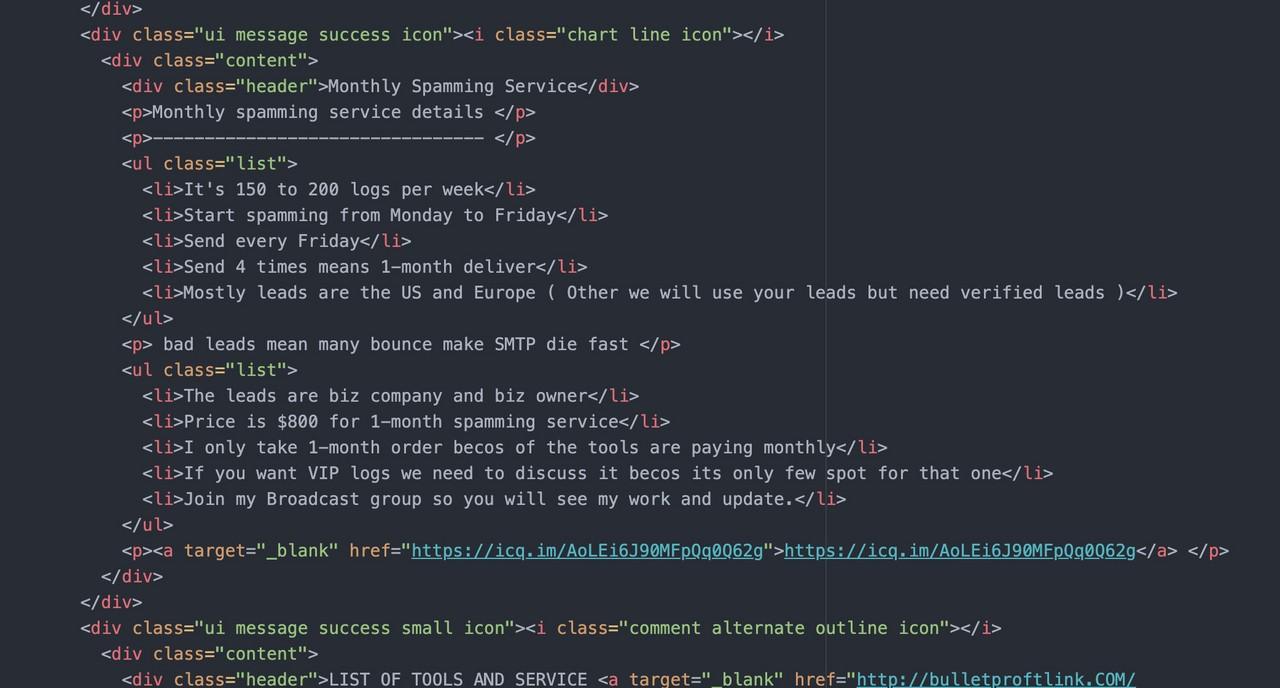
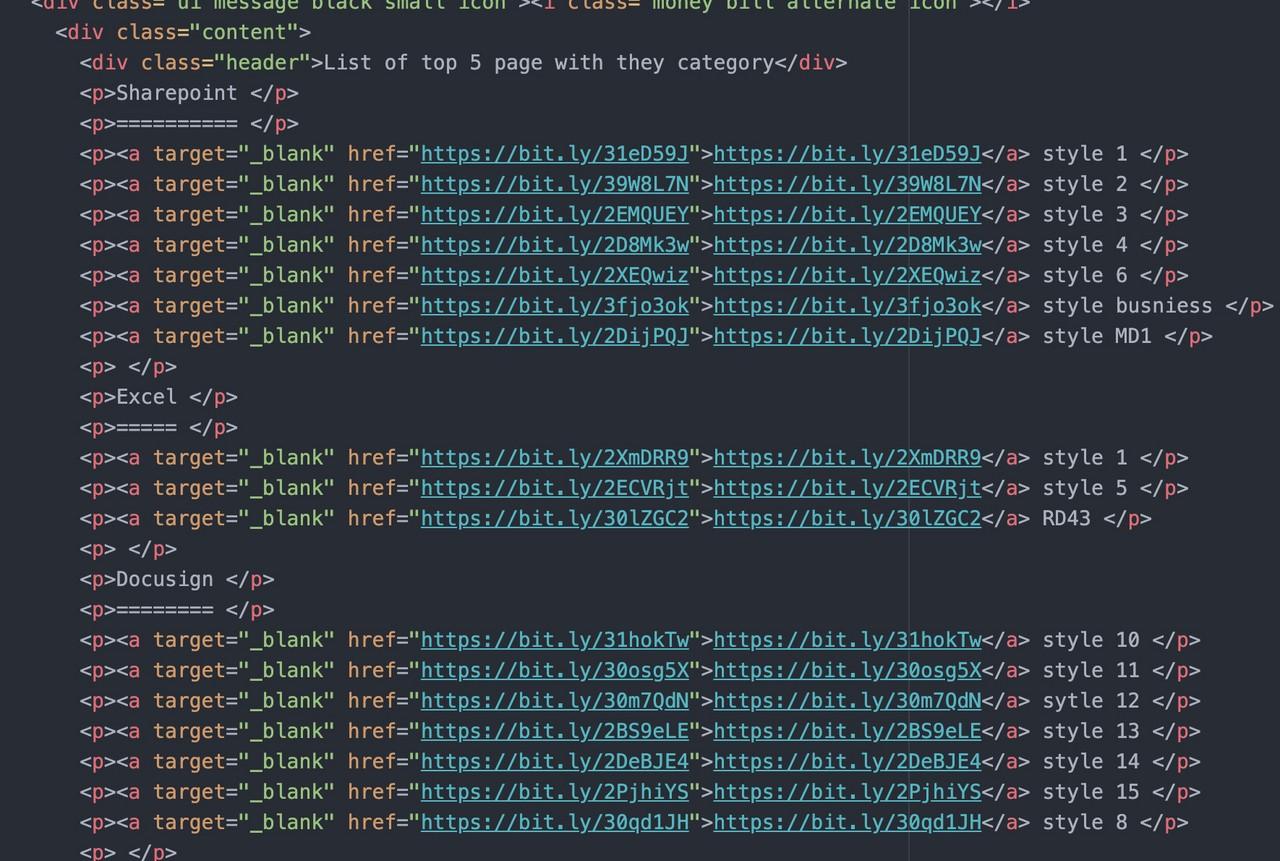
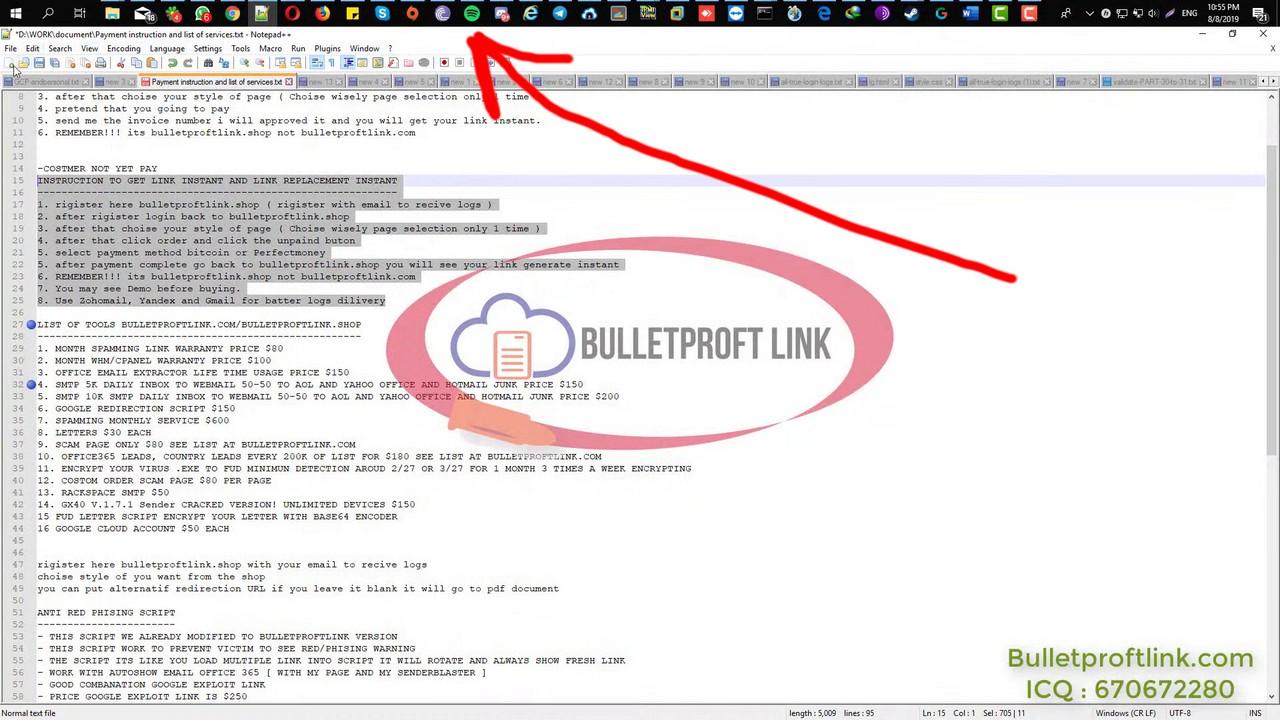
According to the hidden text in the source code (link here), the managed phishing service costs $800 per month. In addition, most of the targets are based in the US and Europe according to the service description.
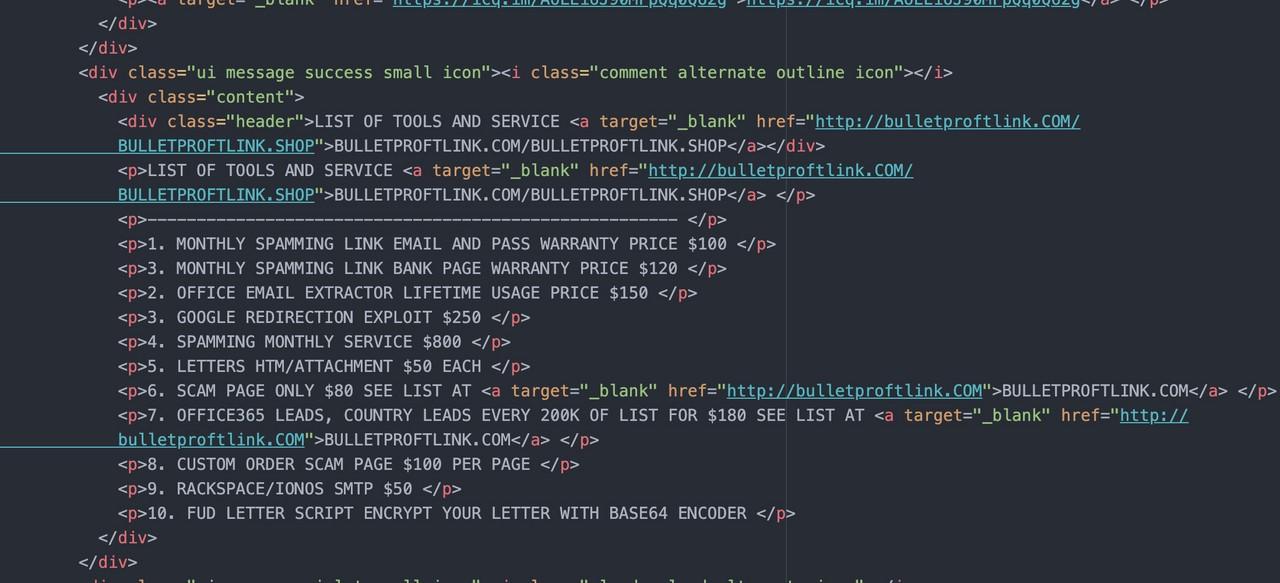
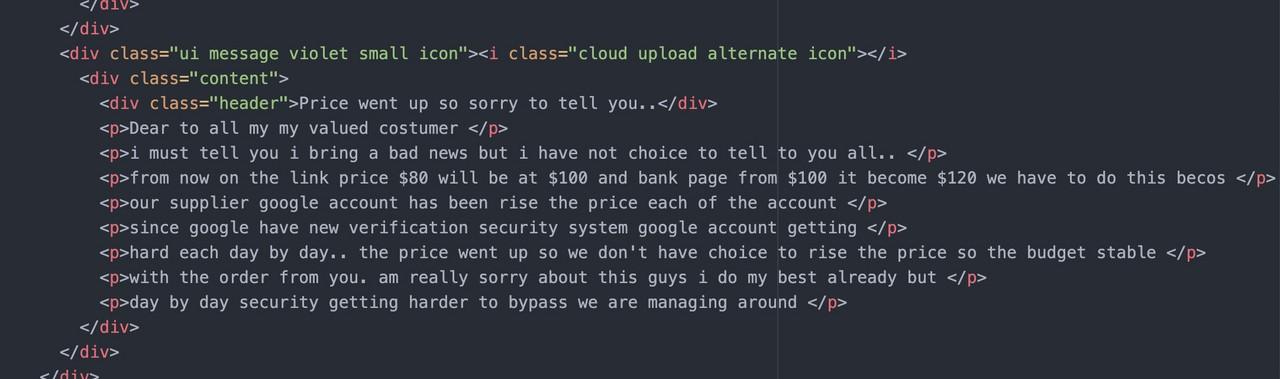
The source code also reveals the top 5 most popular services and samples how the phishing page looks like.
What did we learn?
So, we established that:
- ‘Anthrax Linkers’ and ‘thegreenmy87’ are associated with ‘Bulletproftlink Shop’;
- ‘Bulletproftlink Shop’ is a website selling phishing pages impersonating known brands and services;
- Bulletproftlink is also offering a hosting service for a rather hefty monthly fee; and
- The Bulletproftlink business is online since 2018.
Who is the operator of Bulletproftlink?
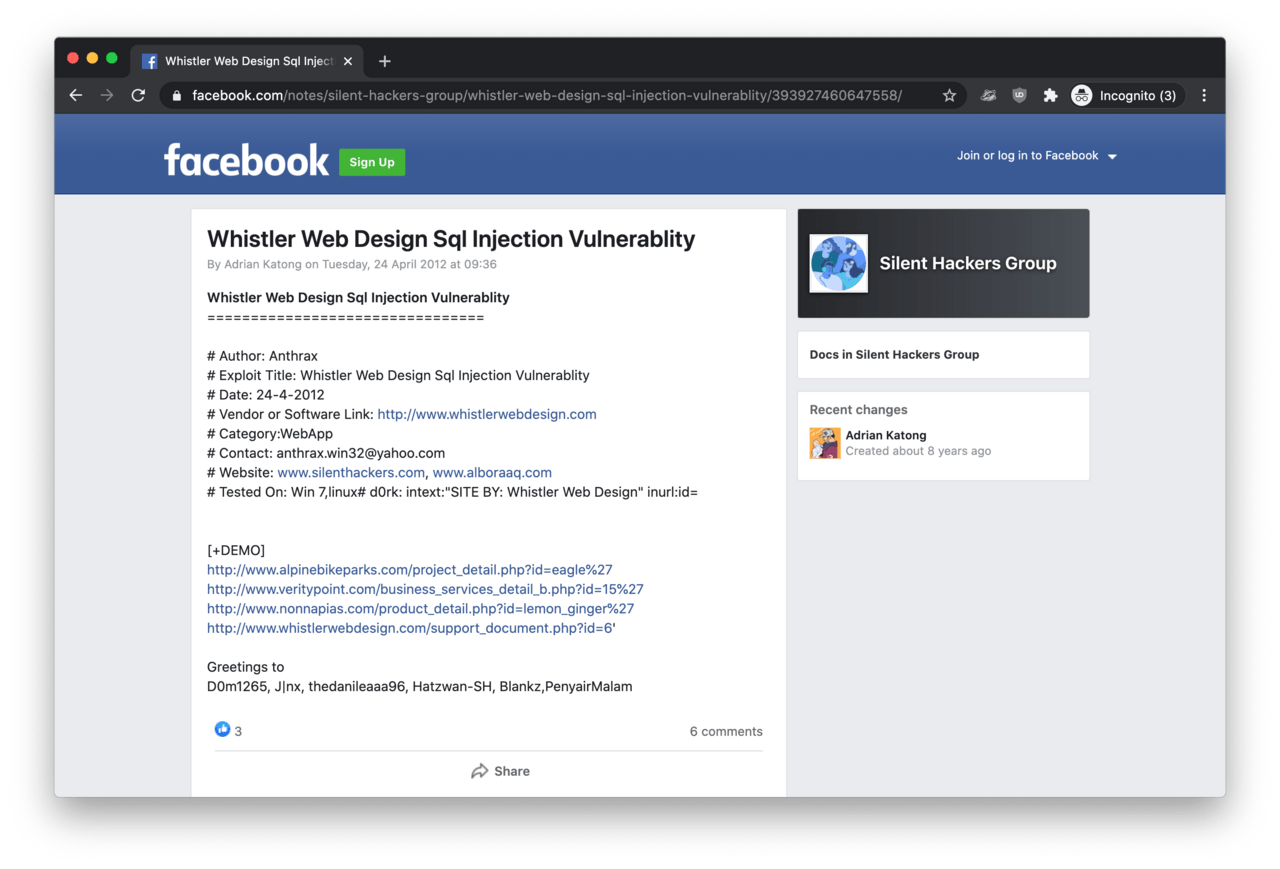
When we took one of the email addresses found on UKBlow and searched for anthrax.win32@yahoo.com, we found an interesting Facebook post from 2012. This was a post about a SQL injection vulnerability in a web application someone found.
What the interesting thing about this eight-year-old post was the author, someone claiming to be ‘Adrian Katong’, and his reference to the email address.
Brief research into this vulnerability Mr Katong posted on Facebook, it seems the researcher and author of the bug report is himself. If he wrote the public announcement of this SQL injection vulnerability announcement, then why was he referencing himself, the author as ‘Antrax’? Also, why was he associating himself with the Anthrax Linkers’s email address anthrax.win32@yahoo.com in the Facebook post?
Further connections with Mr Katong
Mr Katong’s association with the email address can be a coincidence or some sort of mistake.
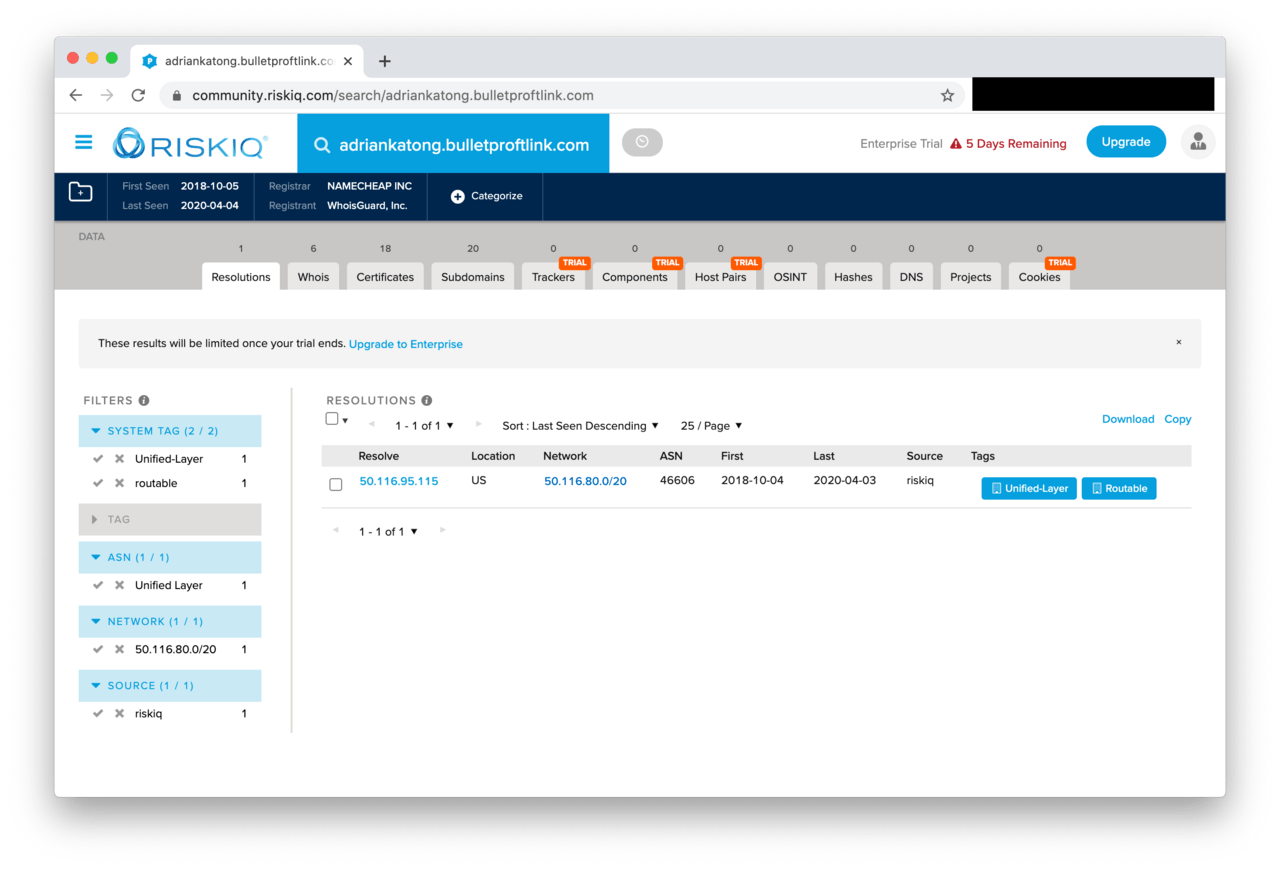
But this begs the question: if we search for the historical subdomain records of .bulletproftlink.com, why there is a DNS record named adriankatong.bulletproftlink.com on Risk IQ?
According to passive DNS records, the subdomain adriankatong.bulletproftlink.com was resolving to 50.116.95.115 between October 2018 and April 2020.
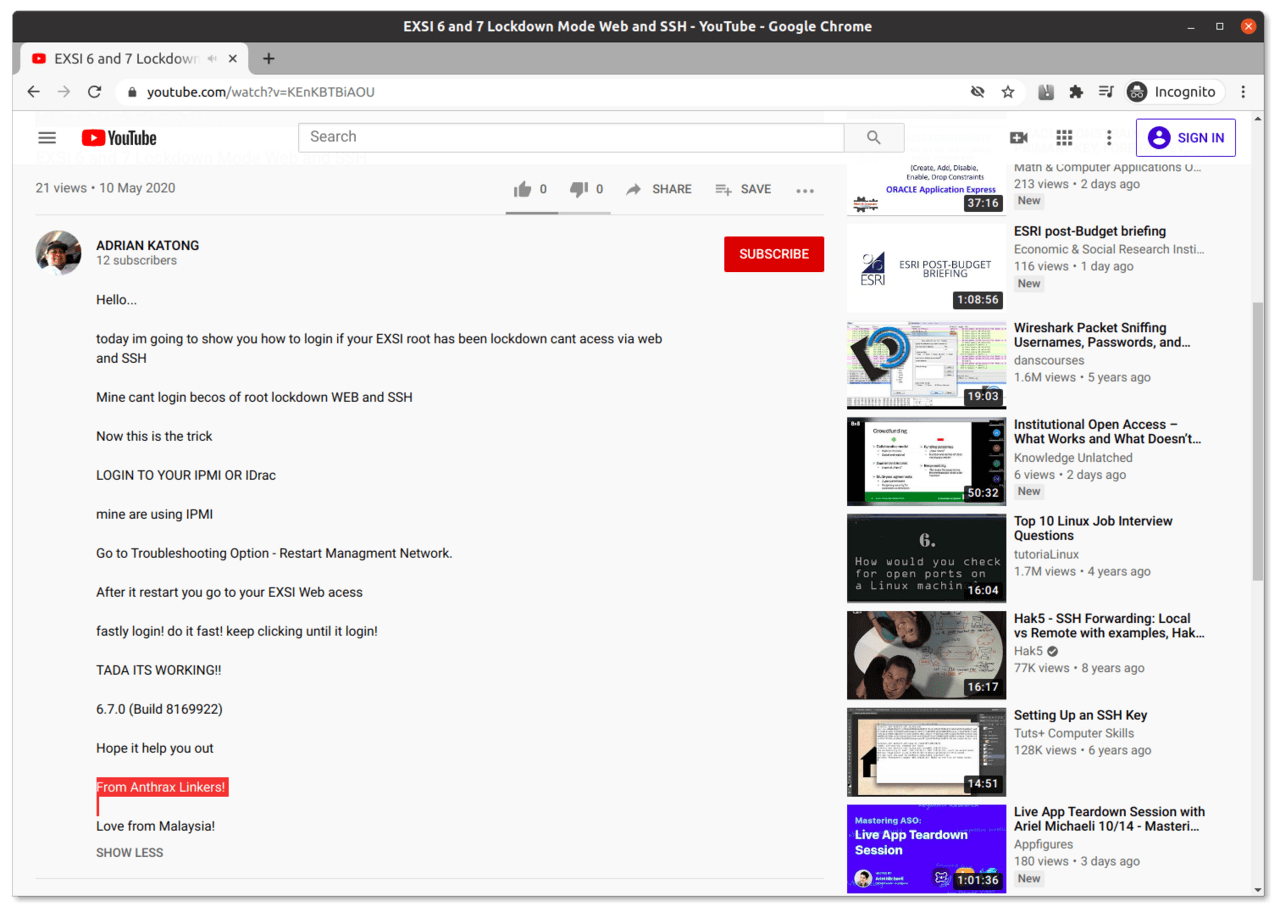
The third clue is a YouTube video appear to be posted by Adrian Katong. In the video description, he signed the video as ‘Anthrax Linkers’ (and places himself in Malaysia).
The ultimate self-own
So all these references can be an eventuality or an elaborate set up framing Adrian Katong as the operator of these damaging phishing campaigns.
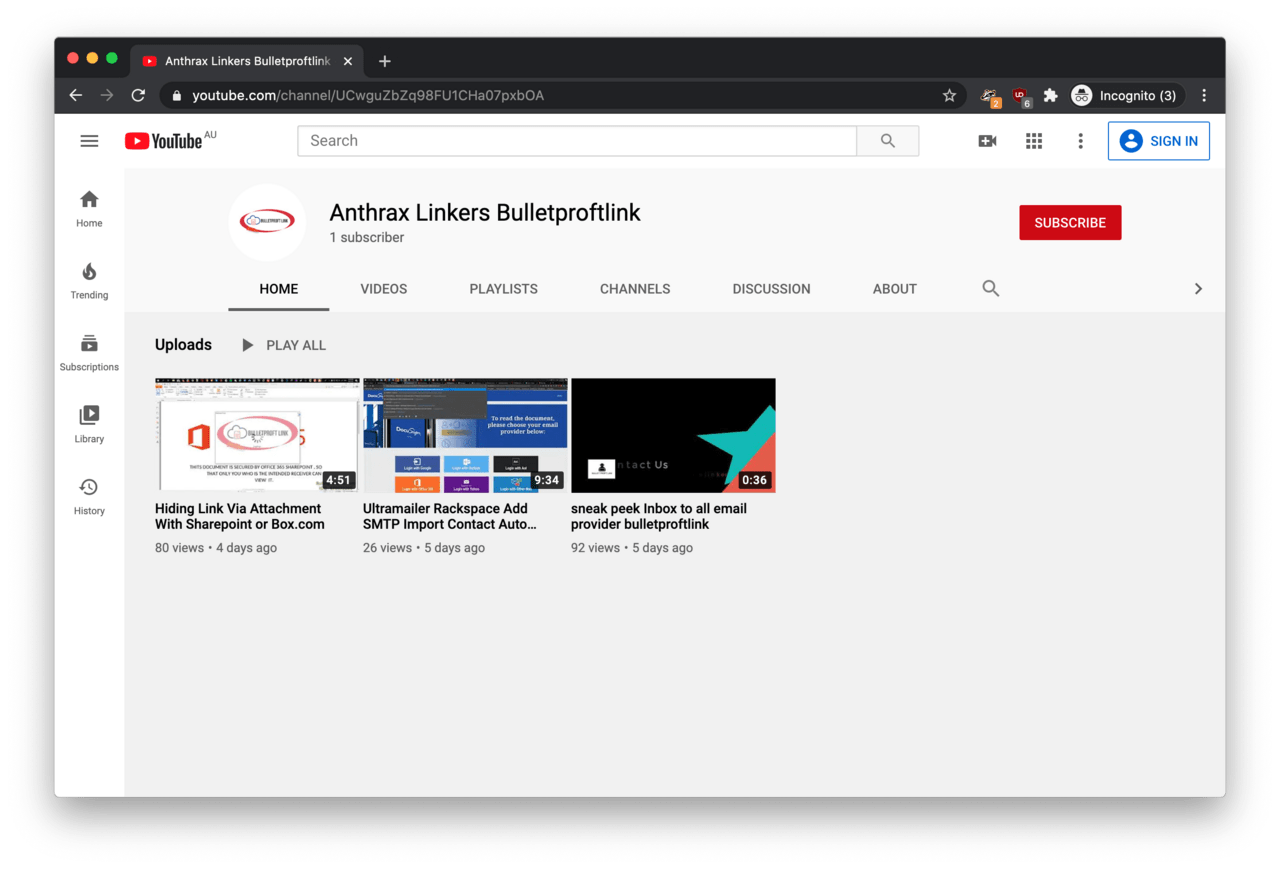
Fortunately, some hard evidence had appeared in October 2020, when someone created a YouTube channel named Anthrax Linkers Bulletproftlink. Needless to say, both the name and logo are all too familiar.
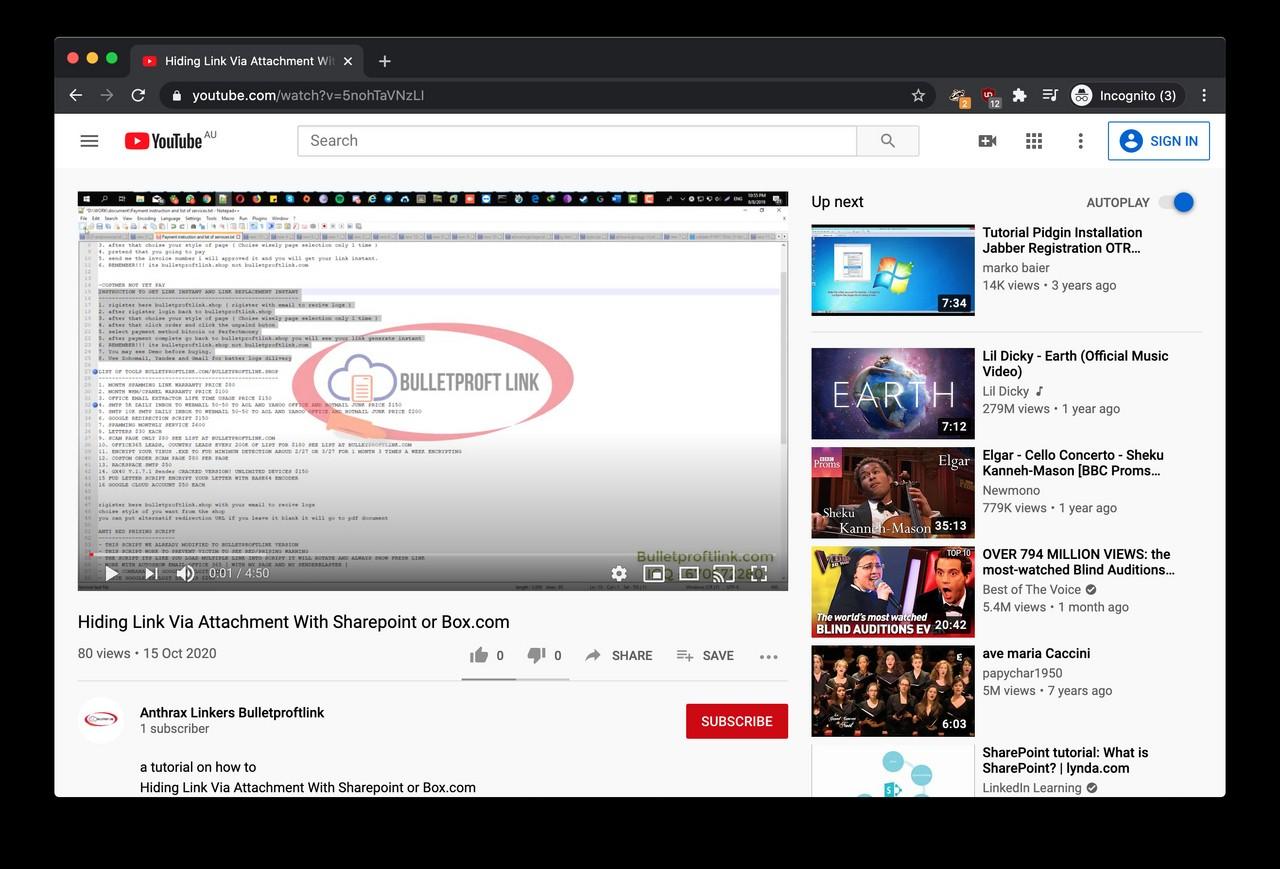
One of the videos (mirror) on the channel is titled as ‘Hiding Link Via Attachment With Sharepoint or Box.com’. This video is a rather convoluted tutorial meant for Bulletproftlink customers, in which someone is demonstrating how to embed a clickable phishing link into a PDF document. The web link in this video (hosted by Bulletproftlink) would take the victim to a fake Microsoft login page.
Let’s analyse the video a bit!
Clue 1.
The first thing we noticed about the Anthrax Linkers screen recording is the unique location of the Windows taskbar on top and the pattern of application icons on the taskbar. A photo on Adrian Katong’s Facebook Page is featuring a photo of a computer (and a cute cat) - interestingly Mr Katong’s screen also features the taskbar on top and the same pattern icons.
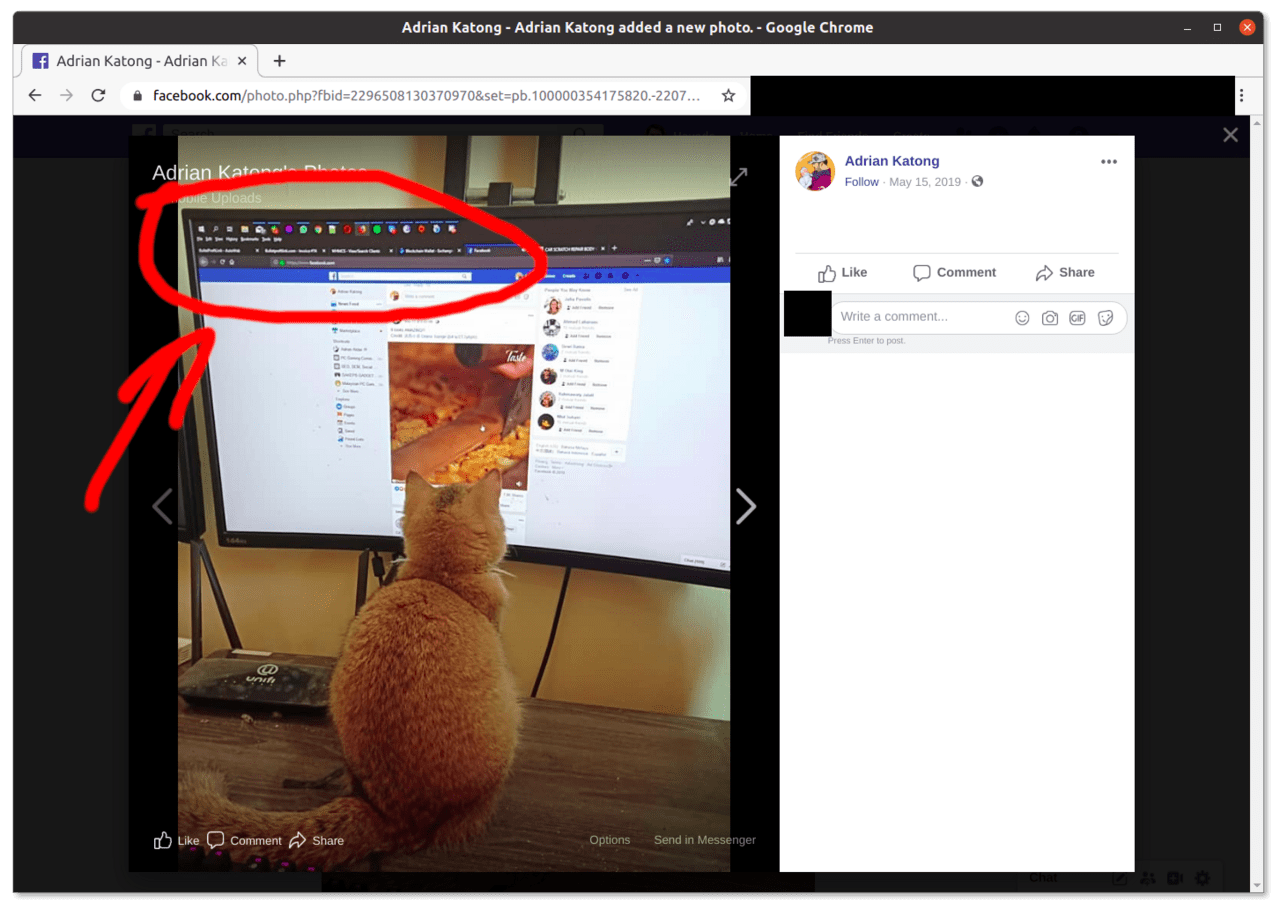
Readers with good eyesight may notice that even the order of the application icons on the top taskbar is similar on both photos: File Explorer, Windows Mail, ICQ, WhatsApp followed by the Opera Browser, Firefox and then Spotify.
Clue 2.
The second most interesting thing is when the publisher of the Anthrax Linkers video is saving a file with Microsoft Word (0:25). When the document is about to be saved, we can see that the Microsoft Word is licensed to ‘Anthrax Linkers’.
The profile picture next to ‘Anthrax Linkers’ looks identical to the photo on Adrian Katong’s YouTube and LinkedIn pages.
Clue 3.
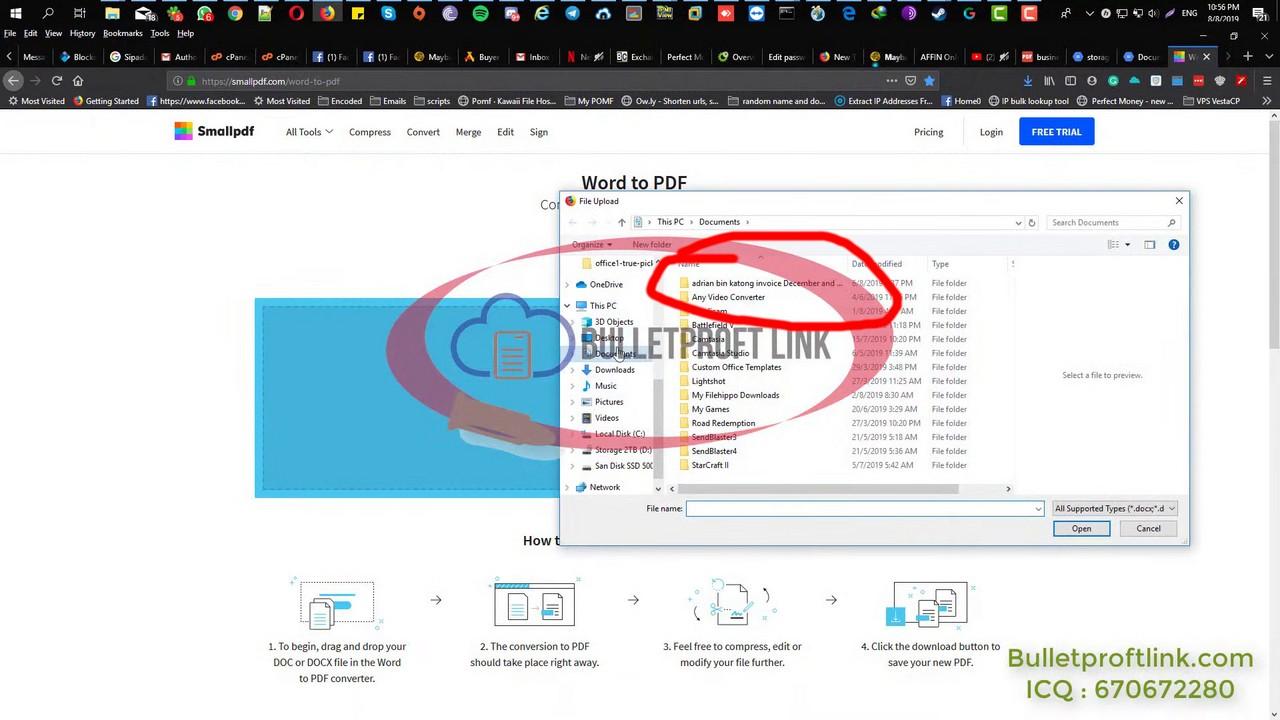
Wait, there are more clues! When the file browser is open (0:55), we can see a directory named arian bin katong invoice December and ....
Clue 4.
The non plus ultra comes at the 3:07 mark of the video when the background music suddenly stops and the video creator is switching to Spotify for a new song.
The top bar of the Spotify app clearly shows that someone is logged into Spotify as ‘Adrian Katong’, while the ADRIAN HIP-HOP PRIVATE COLLECTIONS playlist is open on the screen.
Ironically, the video creator chooses Only God Can Judge Me by 2Pac.
Finally, the cherry on top is when the video creator incriminates his own customers by showing some of the chat histories of his ICQ account.
Summary
In this article, we established with high confidence that someone claiming to be ‘Adrian Katong’ maintains intimate connections with ‘Anthrax Linkers’ and the Bulletproftlink webshop. His website is a one-stop-shop offering phishing pages for sale and phishing services for a flat fee. Both offerings are designed to impersonate a wide range of popular brands and services and to facilitate identity theft.
In Part 3, we are looking into Adrian Katong’s online footprint to find out more of his criminal activities.