Domain Services: A domain name extension scam
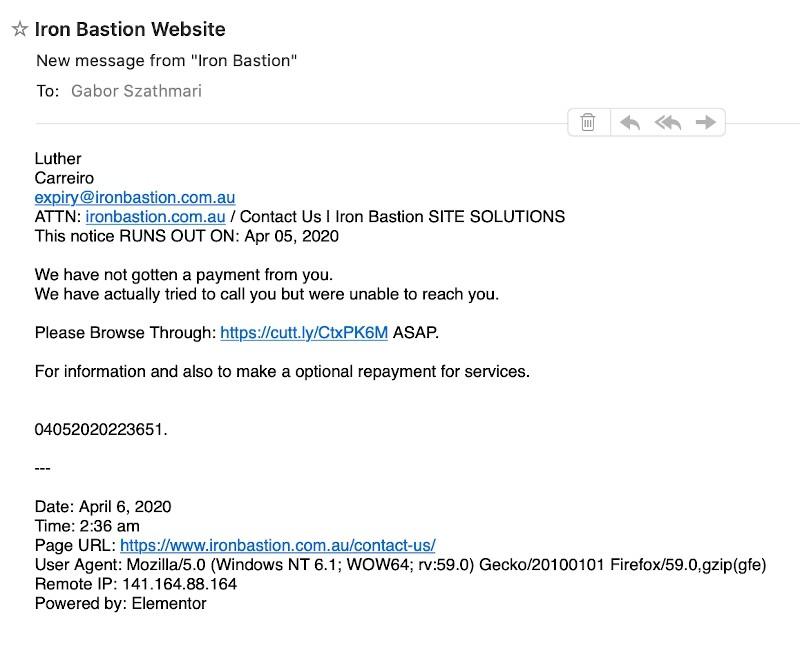
I received this spam other day telling me my business’s domain name is about to expire (no it’s not!). According to the email, I urgently needed to click on this link to extend my domain name.
So, I clicked on the link to see what happens and I managed to find a few pointers to the person presumably running this particular domain name slamming operation.
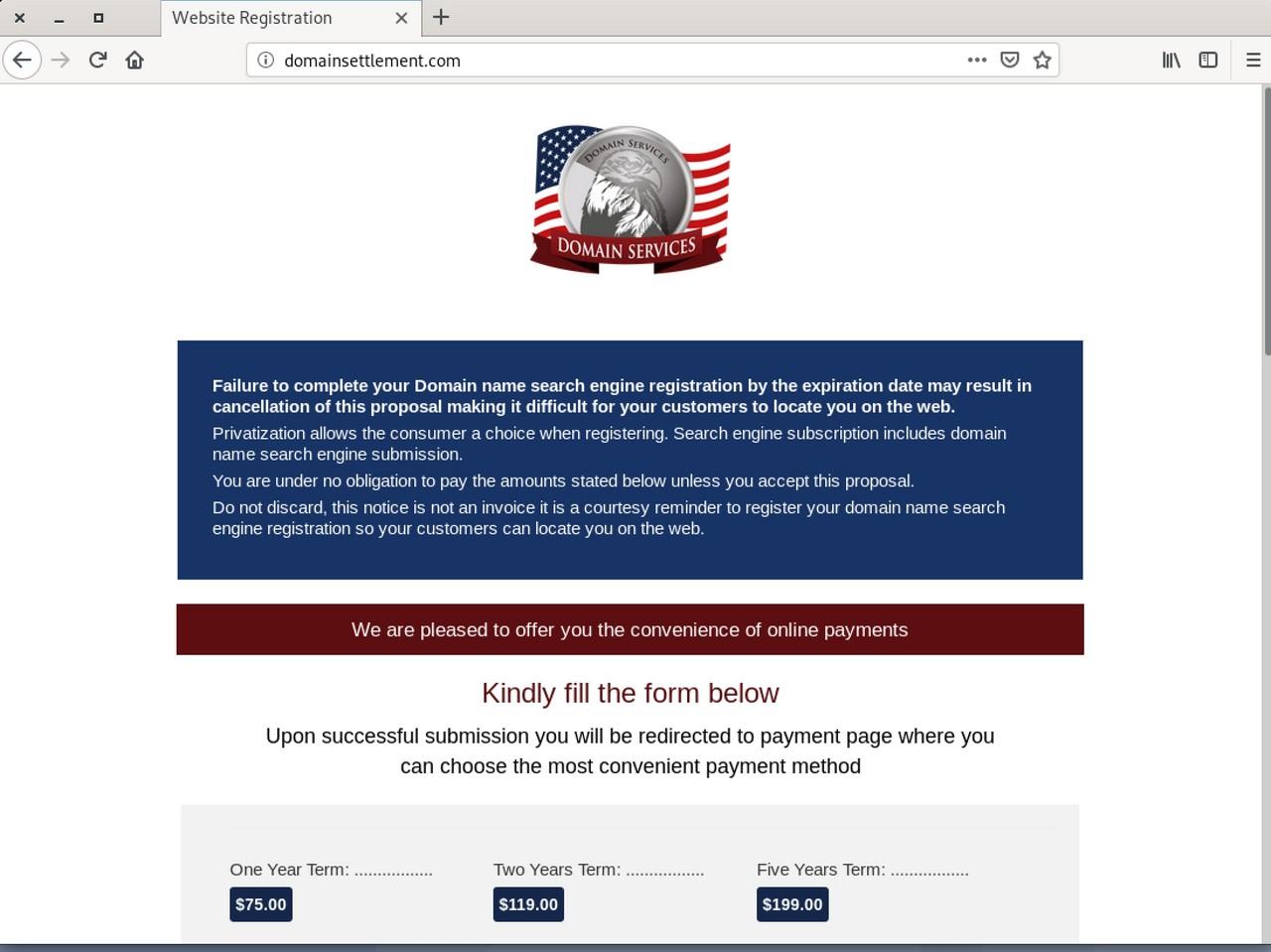
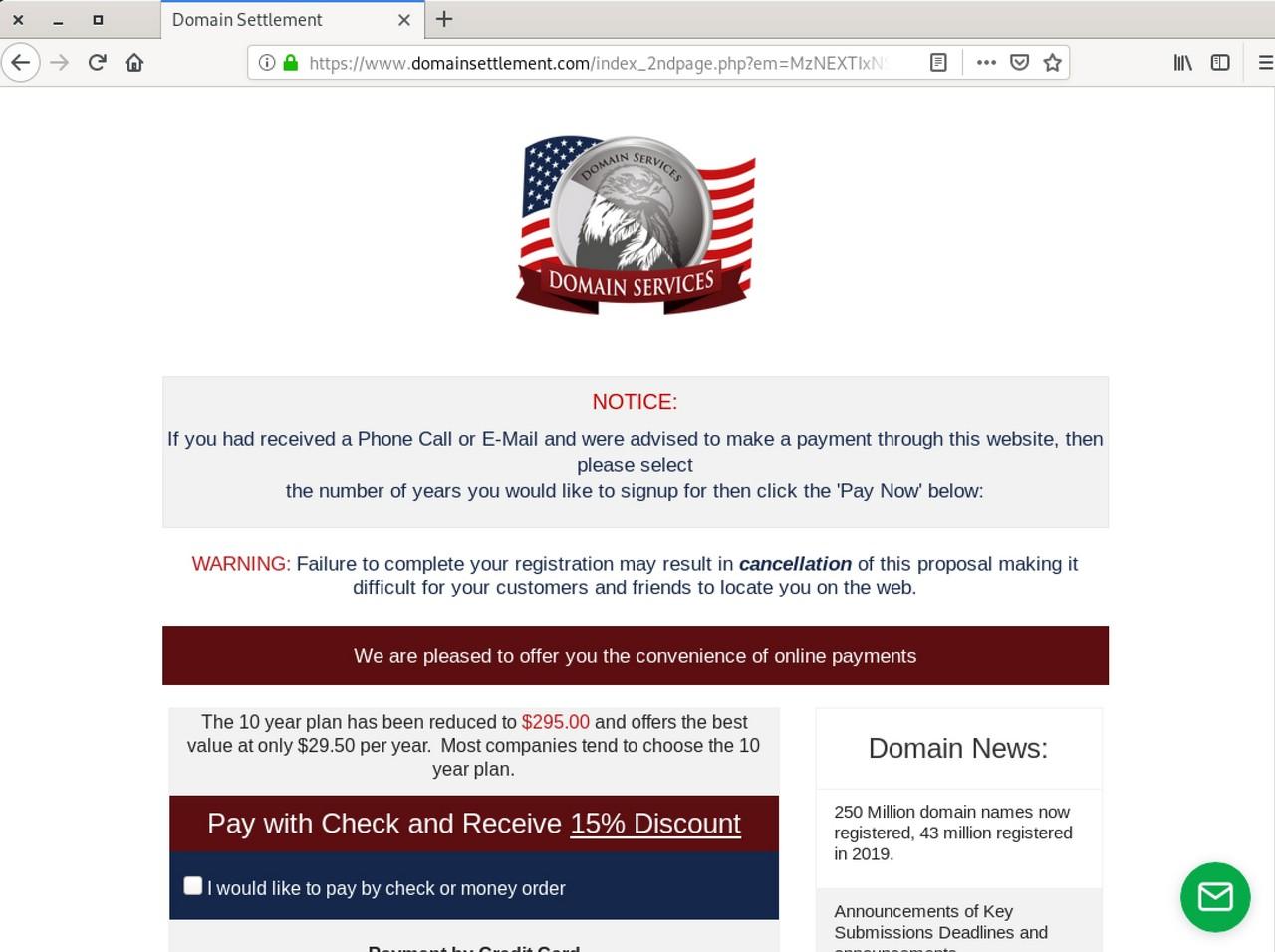
The link in the email took me to a page that appears to be some kind of domain name ordering portal, which may come across as legitimate to the technically challenged.
Presumably, the target audience of the spam campaigns is business owners with limited understanding of IT. This audience may have the impression that Domain Services is somehow associated with their business’s domain name and their presence on Google – so they end up paying.
The order flow
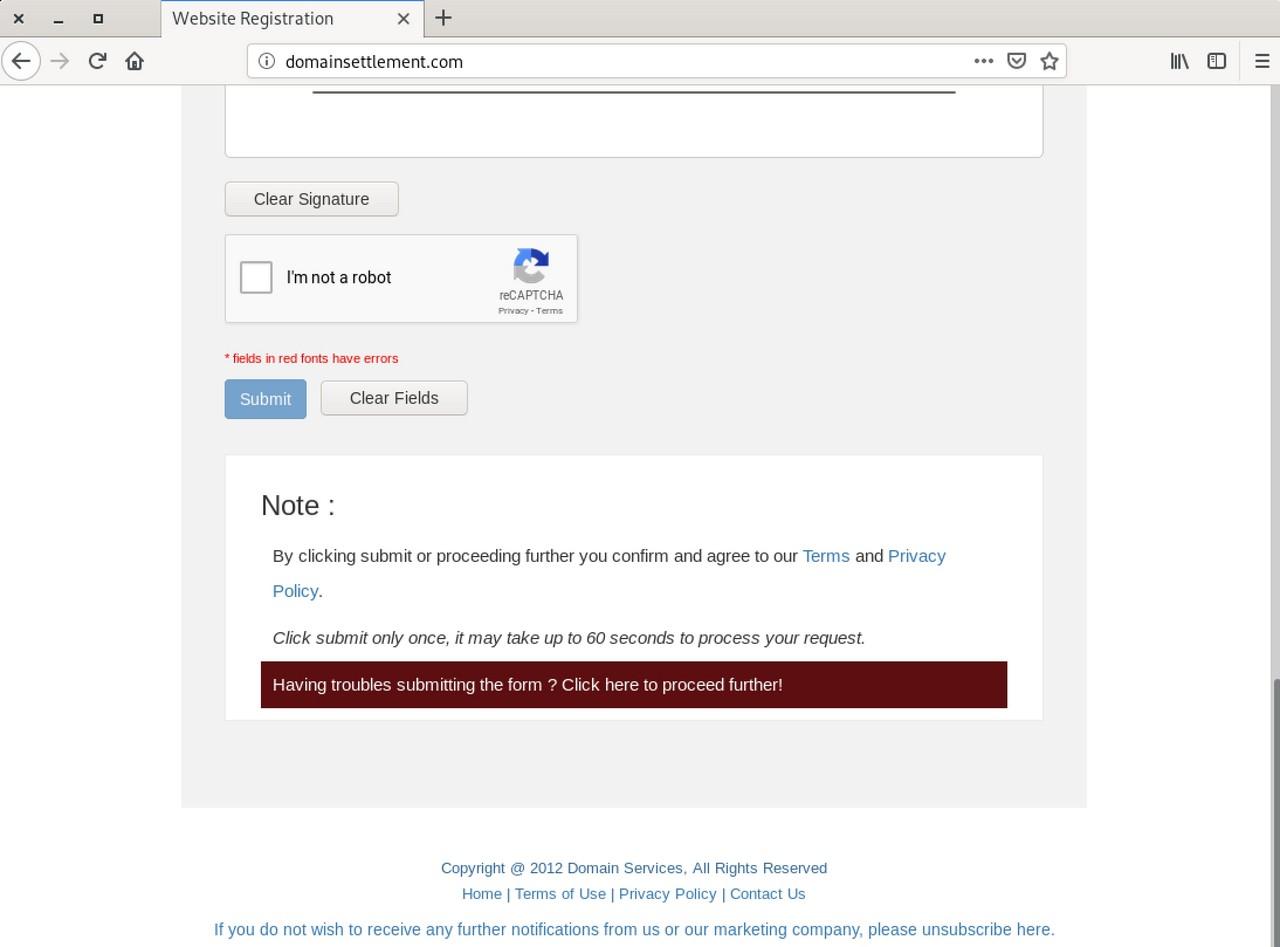
Once we fill in the details, the checkout flow takes us to the next page further claiming that “failure to complete your registration may result in cancellation” if the domain name is not extended right away.
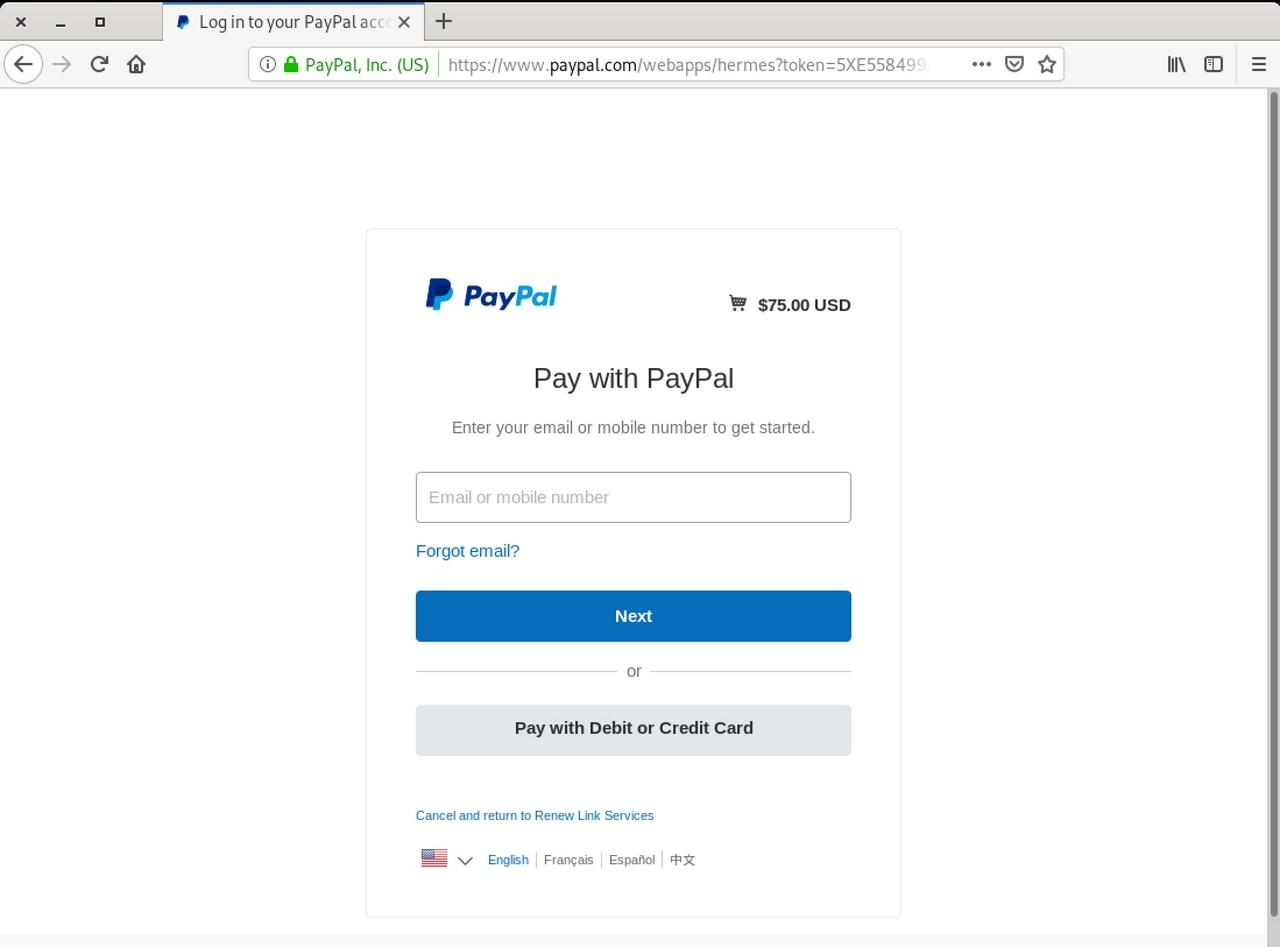
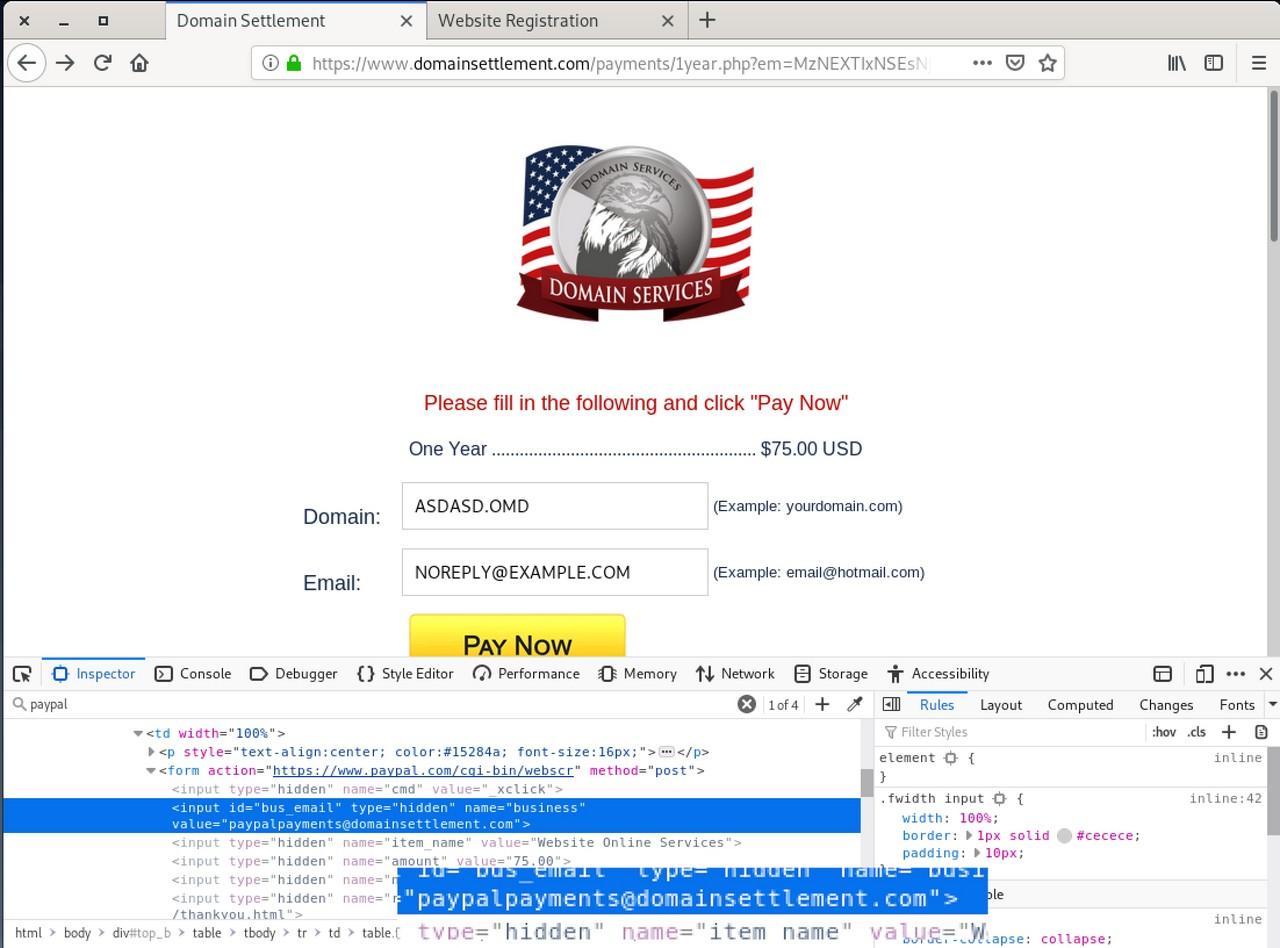
Once we click on the “Pay Now” link, the page takes us to the real PayPal checkout page to my surprise. The source code at PayPal reveals the name of the destination wallet is paypalpayments@domainsettlement.com.
The larger ‘Domain Services’ network
Domain Services uses different domains to get around spam filters and blacklists, presumably. Further investigation using open-source data reveals a handful of additional websites associated with the scam.
After some careful analysis, I managed to identify the following domain names associated with Domain Services:
dnremit.com
domainremit.com
domainremits.com
domainservicesboard.com
domainsettlement.com
nameremit.com
remitnotice.com
renewzone.com
siteremit.com
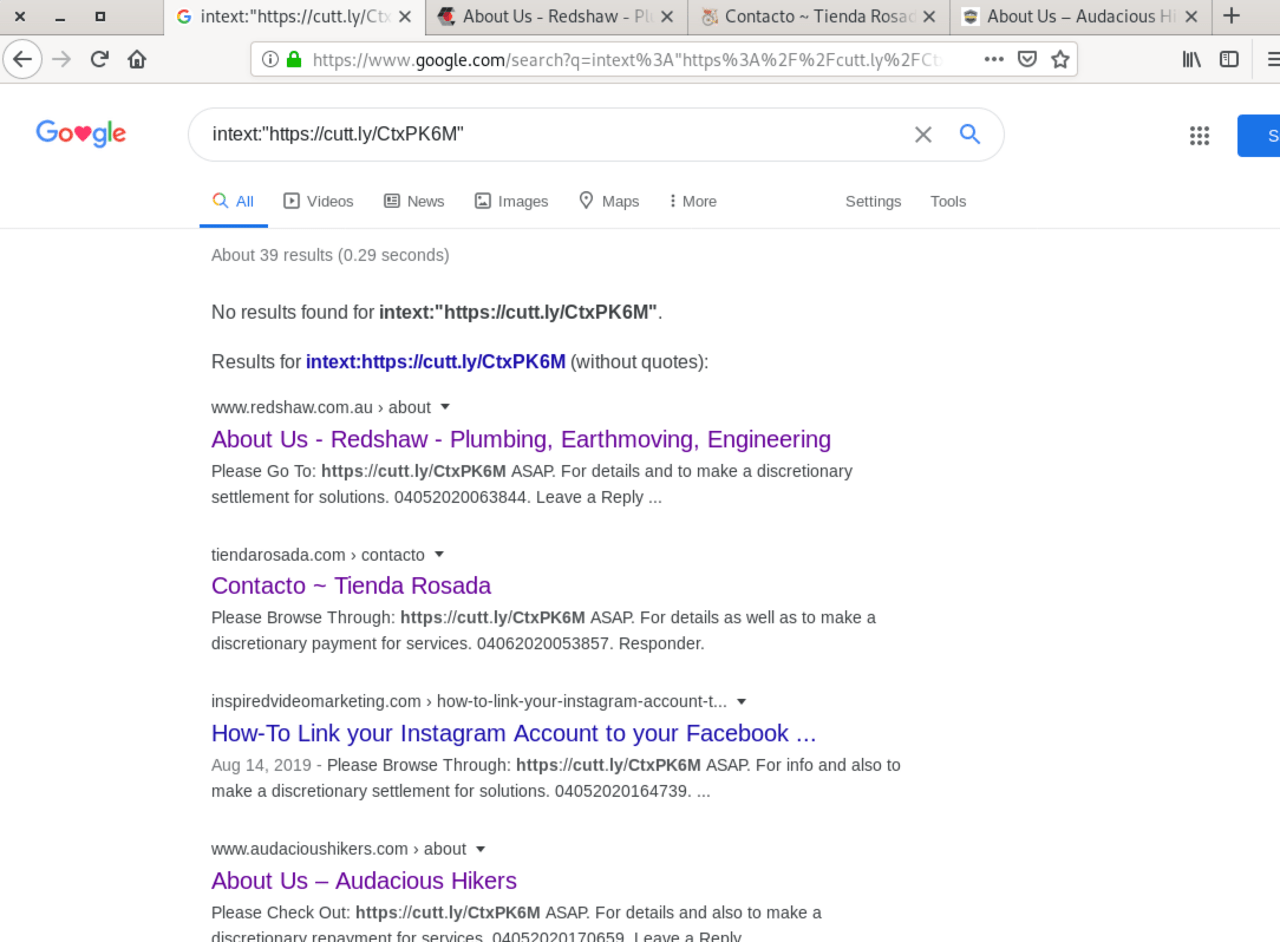
Domain Services seem to advertise with spamming on forums and comment forms.
So who owns Domain Services?
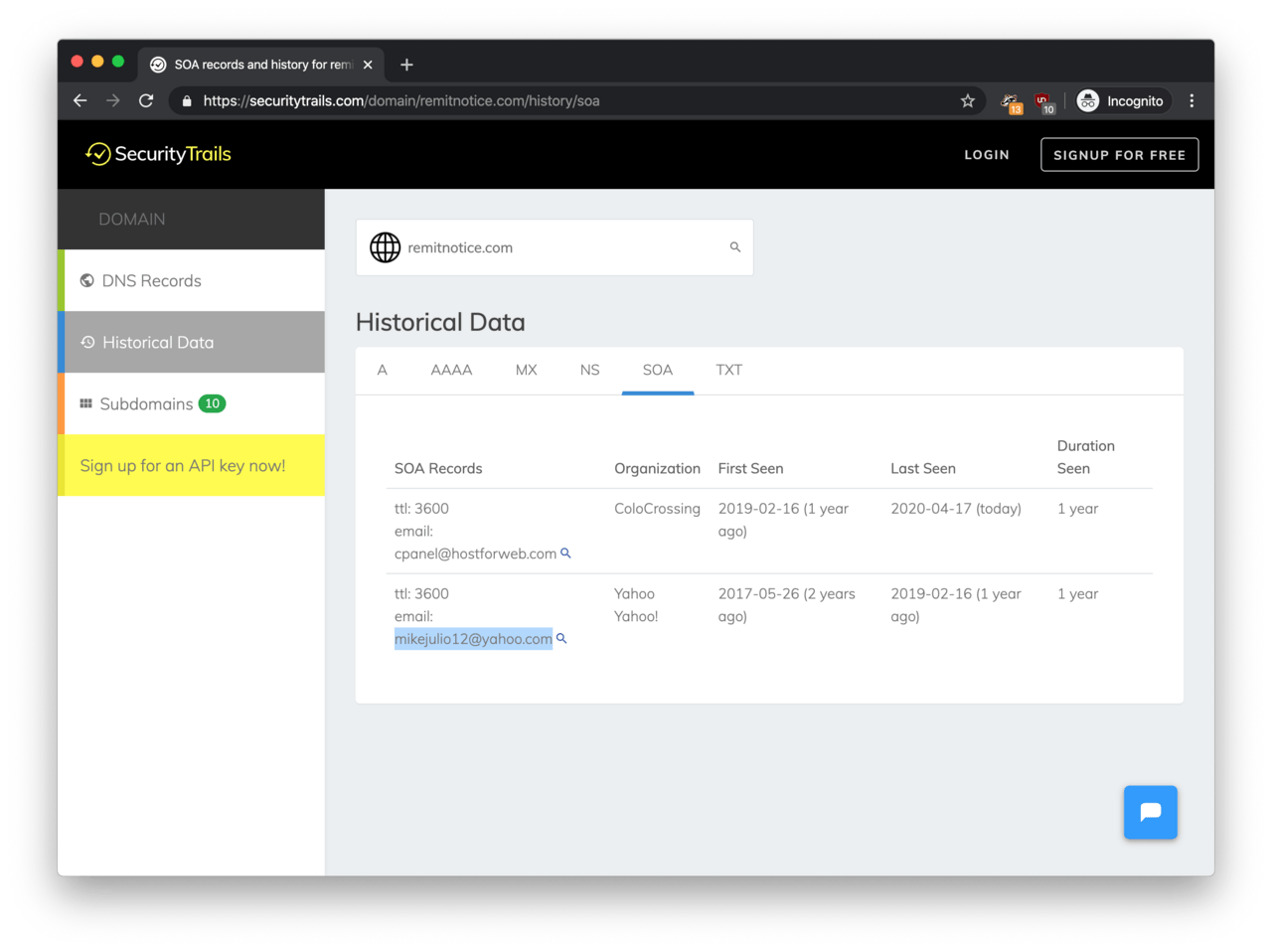
The first pointer was an email address I stumbled upon in the historical WHOIS details of the domains from above.
According to SecurityTrails, remitnotice.com featured the email address mikejulio12@yahoo.com on the WHOIS records at one point.
So we have an email address, let’s pivot on this one!
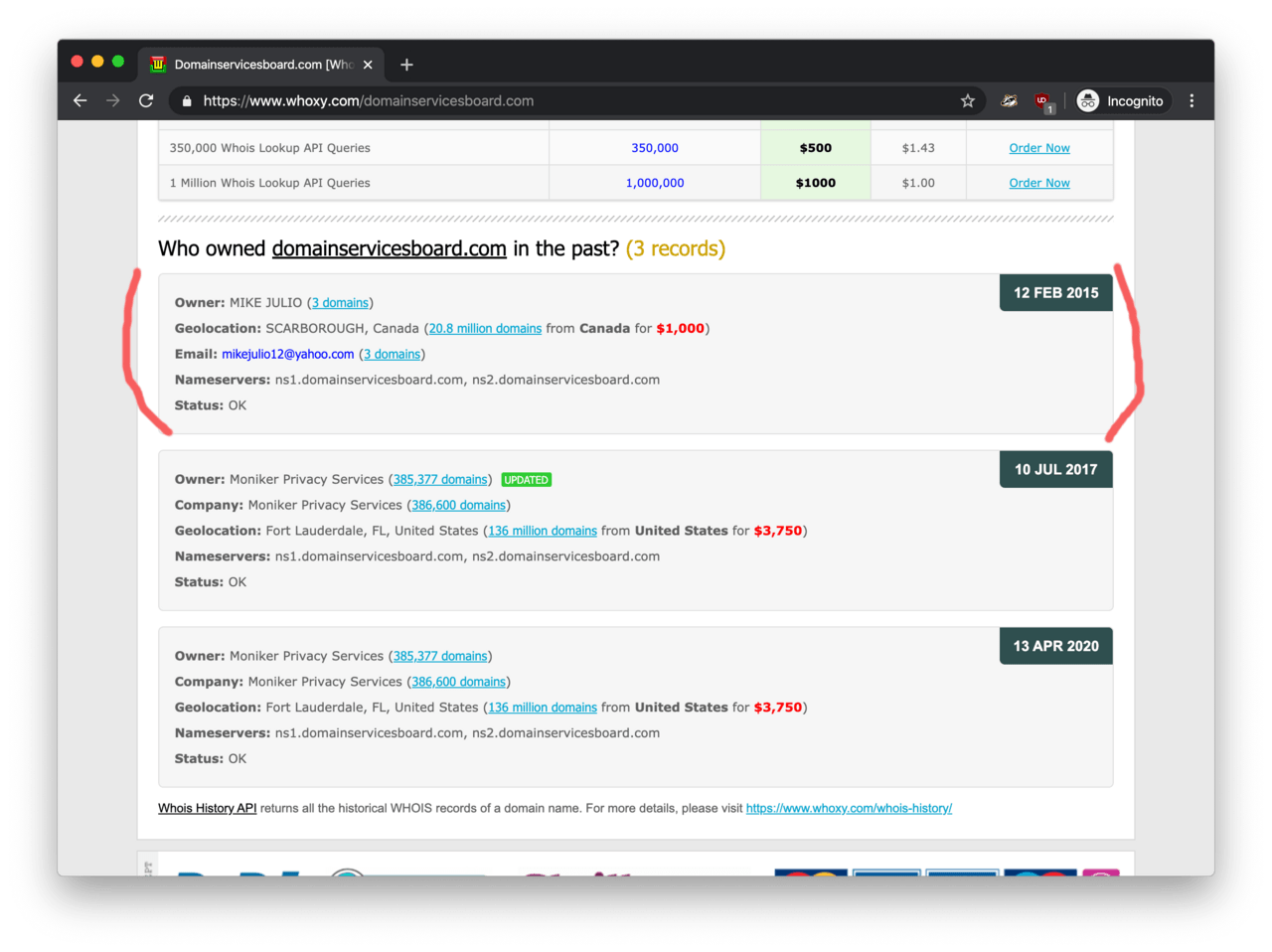
Although every domain name has domain privacy turned on, I was lucky to find that DomainServicesBoard.com did not have the domain privacy enabled in the past. According to Whoxy, Mike Julio from SCARBOROUGH, Canada was the owner back in 2015.
Bear in mind that WHOIS data could be fake as the contact details are not verified by the domain registrant upon registration.
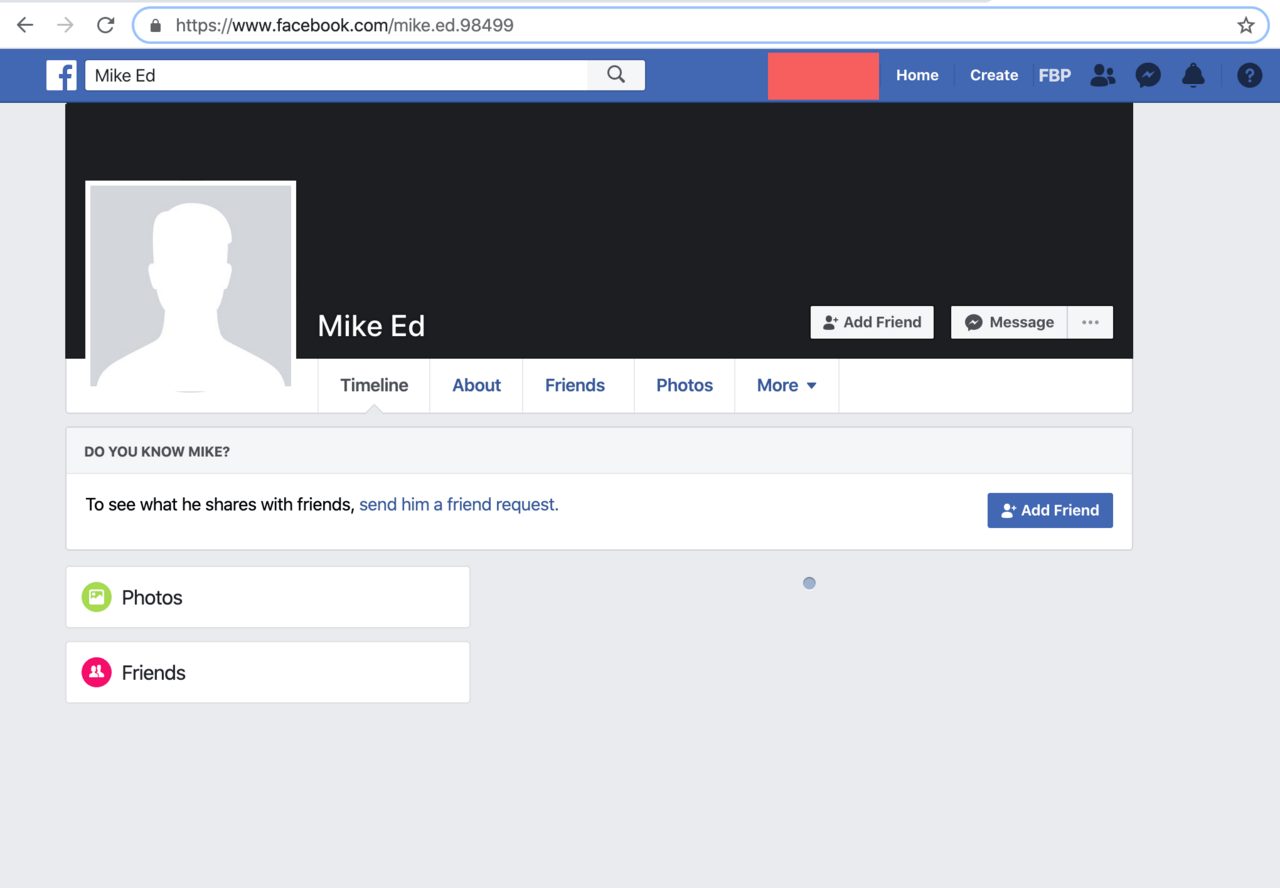
By using the email address from the newly found WHOIS record, I managed to identify the Facebook and LinkedIn profiles of Mike Julio.
Unfortunately, both profiles are probably fake as both pages are suspiciously empty. Also, the last name on the Facebook profile is ‘Ed’ instead of ‘Julio’. According to Have I Been Pwned, the email address was never involved in a data breach suggesting that this email address was a throwaway.
A potential business connection
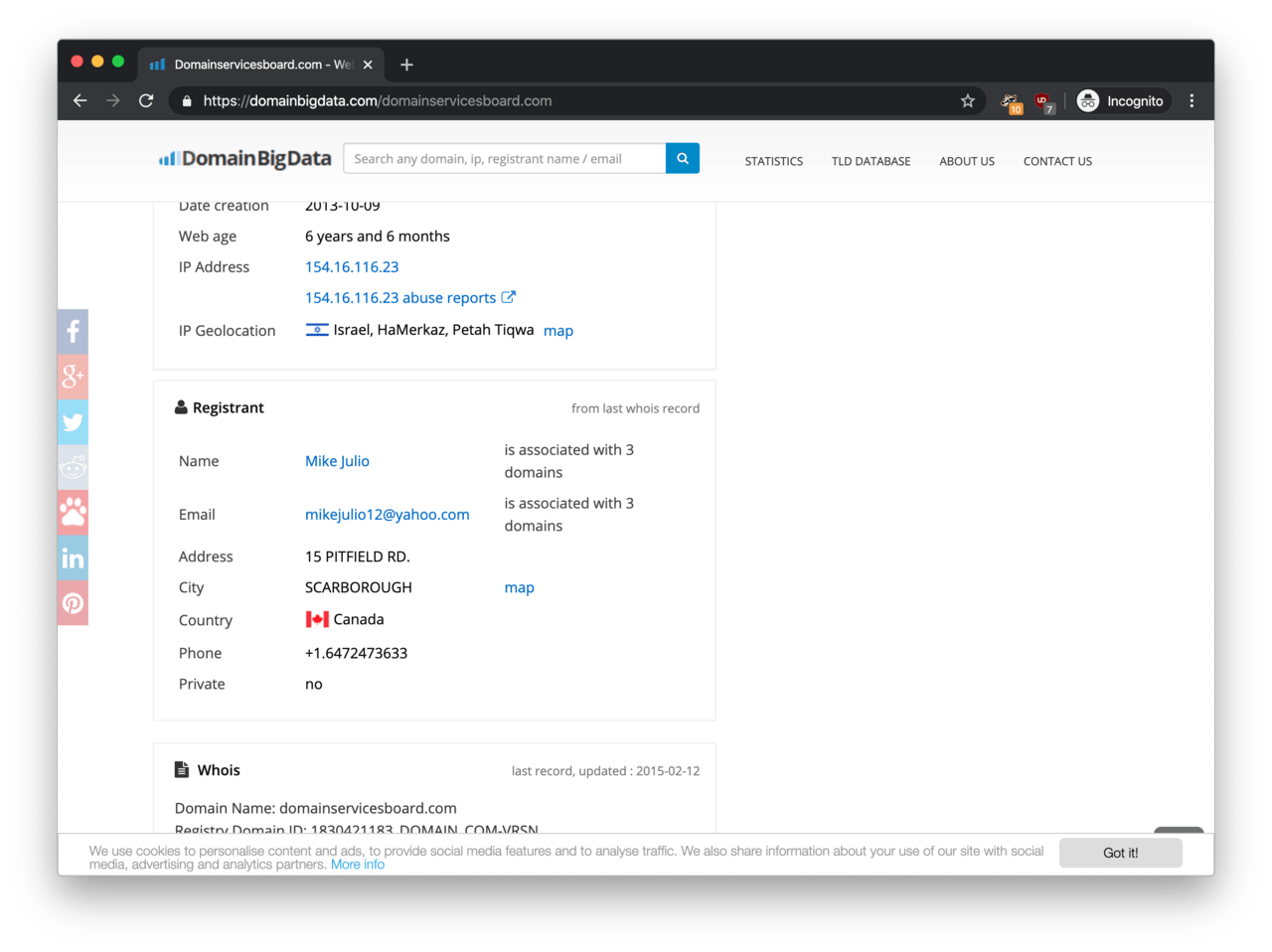
I almost gave up at this point, when I found Mike Julio on DomainBigData.com by accident. To my surprise, DomainBigData gave me the full address from the WHOIS record.
According to DomainBigData, the full address of Mike Julio is 15 PITFIELD RD., SCARBOROUGH, Canada, which partially matches the results from Whoxy from earlier. It got me a phone number as well: +1.6472473633. Wow!
Ting Zhang
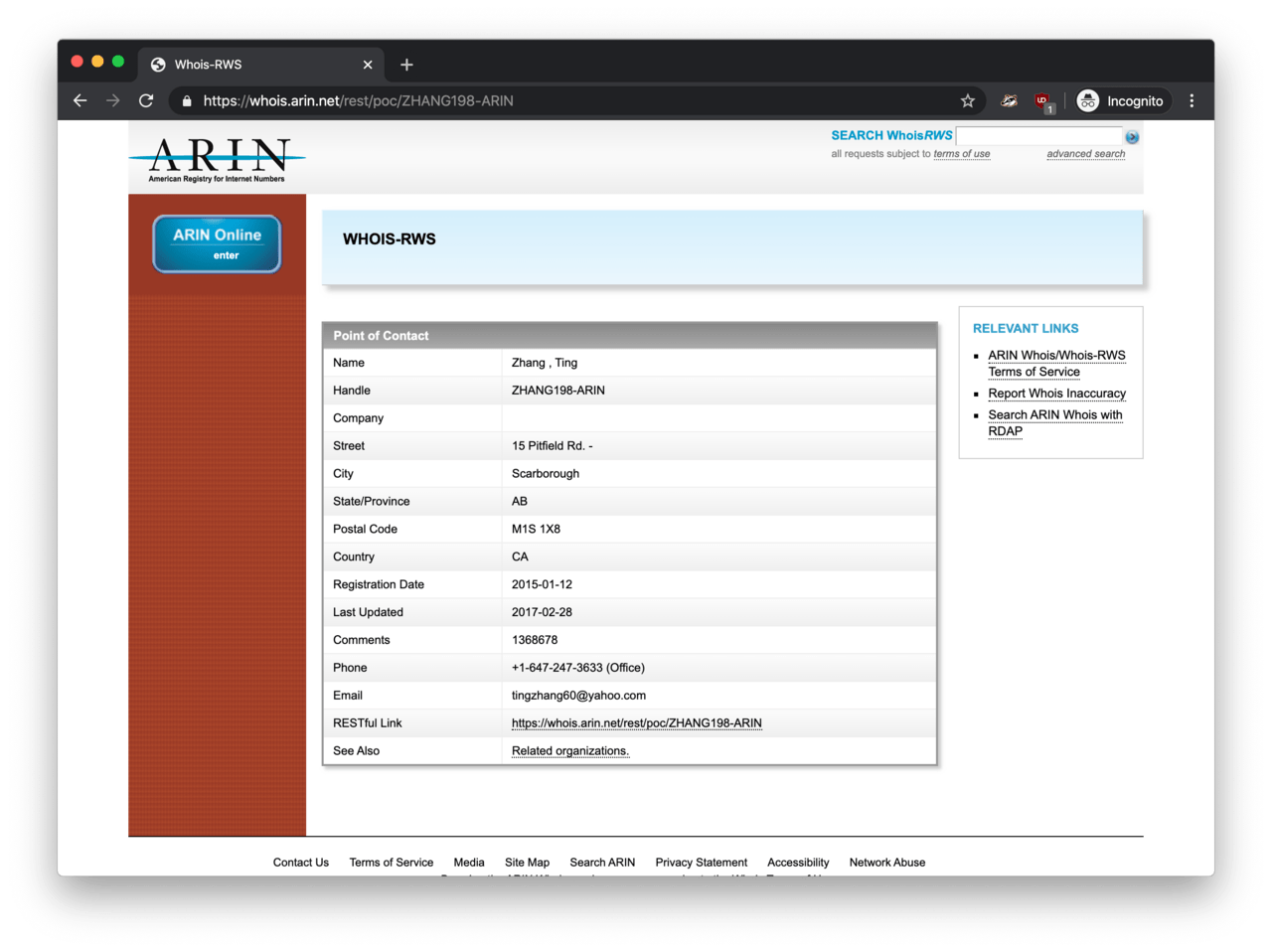
The first pivot point was the phone number, which I found on the ARIN portal. This phone number featured on a WHOIS record along with the Scarborough address. But look! We have a different name and email address here: Ting Zhang and tingzhang60@yahoo.com. Unfortunately, I did not manage to find anything about Mr Zhang.
Loong Information Services Inc.
Now, this is where the leads are getting weak.
Just as a reminder, the full address on the WHOIS record of DomainServicesBoard.com is 15 PITFIELD RD, SCARBOROUGH, M1S 1X8, CANADA.
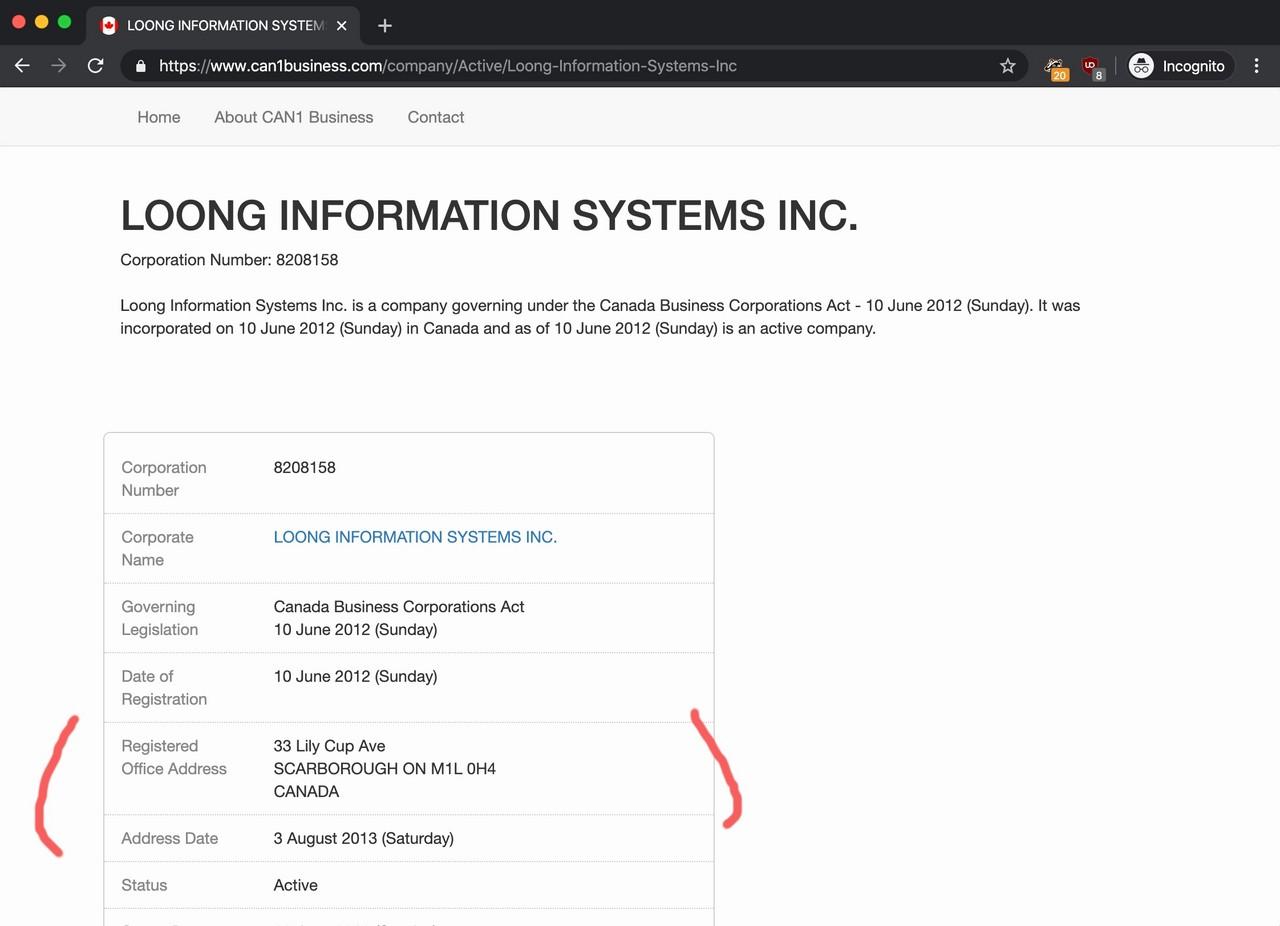
According to a companies register, a business named LOONG INFORMATION SYSTEMS INC. was also registered at 15 PITFIELD RD between 2012 and 2013.
There is a potential connection between Domain Services and LOONG INFORMATION SYSTEMS INC.:
-
One of the Domain Services domains (DomainServicesBoard.com) was registered in October 2013 according to the historical WHOIS records;
-
DomainSettlement.com dates itself back as far as 2012 on the bottom of the ‘contact us’ page.
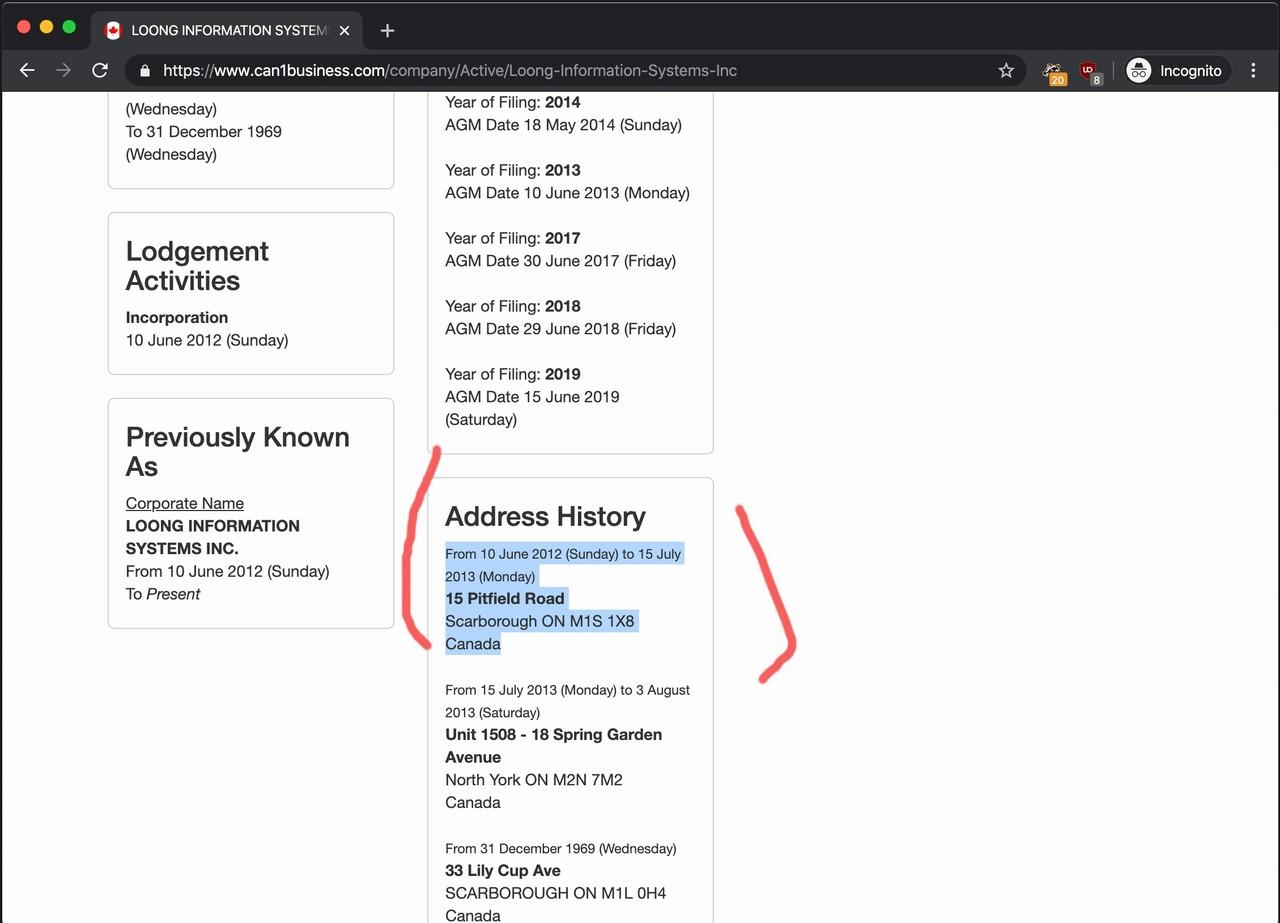
- DomainServicesBoard.com had the same address on the historical WHOIS record as LOONG INFORMATION SYSTEMS’s registered address around in 2012/2013;
As for the owner of LOONG INFORMATION SYSTEMS INC., the sole director is Zhihong Lu according to a second company register and the company documents I ordered online. Sadly, I did not find much about Mr Lu and I concluded my search at this point.
Summary
So just to shortly summarise how Domain Services and LOONG INFORMATION SYSTEMS INC. may have some connections with each other:
-
The DomainServicesBoard.com domain name was registered at 15 PITFIELD RD. around 2013.
-
The Copyright text on the bottom of DomainSettlement.com claims that ‘Domain Services’ is live since 2012.
-
LOONG INFORMATION SYSTEMS INC. was a registered business at 15 PITFIELD RD. between 2012 and 2013.
-
The director of LOONG INFORMATION SYSTEMS INC. is Zhihong Lu since 2012.
Disclaimer
The chain of evidence comes with a big disclaimer. The association with LOONG INFORMATION SYSTEMS INC. could be merely a coincidence because there is no guarantee that the details on the WHOIS records were accurate in the first place. After all, anyone can register a domain name with a fake or non-existent name and address added to the WHOIS record. In this case, there is a possibility that someone impersonated LOONG INFORMATION SYSTEMS INC. back in 2015 to register some of the domain names associated with Domain Services.
Therefore, there is no conclusive evidence that LOONG INFORMATION SYSTEMS INC. and Zhihong Lu is associated.
Conclusion
Various consumer protection groups such as Fraudwatch and ACCC is a great source of information on avoiding domain slamming scams associated with domain name registrations and extensions.
Domain Services seems to be running its bogus domain extension services on a range of websites since 2012. As opposed to a legitimate business, none of the websites features the name, business registration number and company details of the registered business running Domain Services.
Investigation using open-source data indicate that the owner of these domains made a generous effort to hide the real identity of the operator or operators of these websites – which a legitimate business would possibly never do.